Ghostly Persistence Write-Up
1. Download and Extract: Start by downloading the provided zip file and extracting its contents.
2. Identify Logs: Upon inspection, we notice the presence of Windows Event Logs.
3. Extract Event Logs: Use the `EvtxCMD` tool from Eric Zimmerman's toolkit to process the Event Logs.
4. Convert to CSV: Run `EvtxCMD` on the extracted directory to generate a CSV file containing the logs.
5. Load into Timeline Explorer: Open the CSV file in `TimeLineExplorer` to analyze the logs.
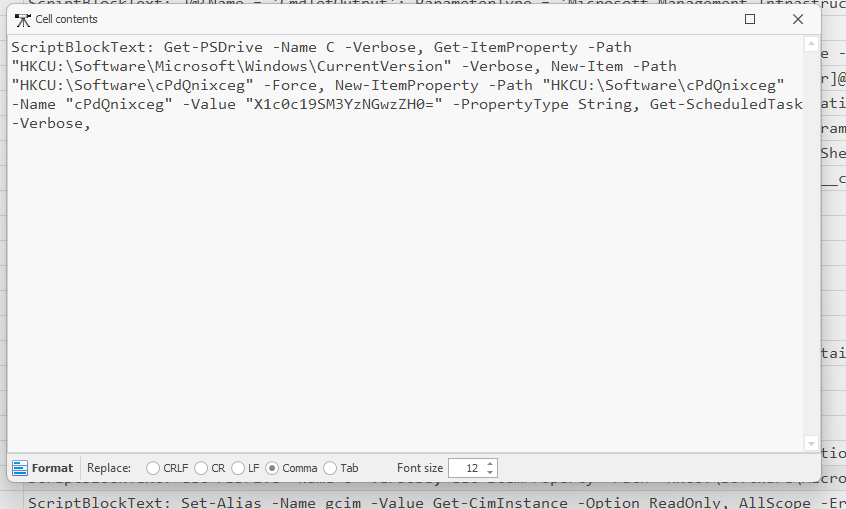
6. Search for Encoded Scripts: Within the logs, we observe paths that indicate encoded PowerShell scripts.
- First Path: `C:\Users\usr01\AppData\Local\Temp\wLDwomPJLN.ps1`
- Inspecting the payload data reveals base64-encoded content:
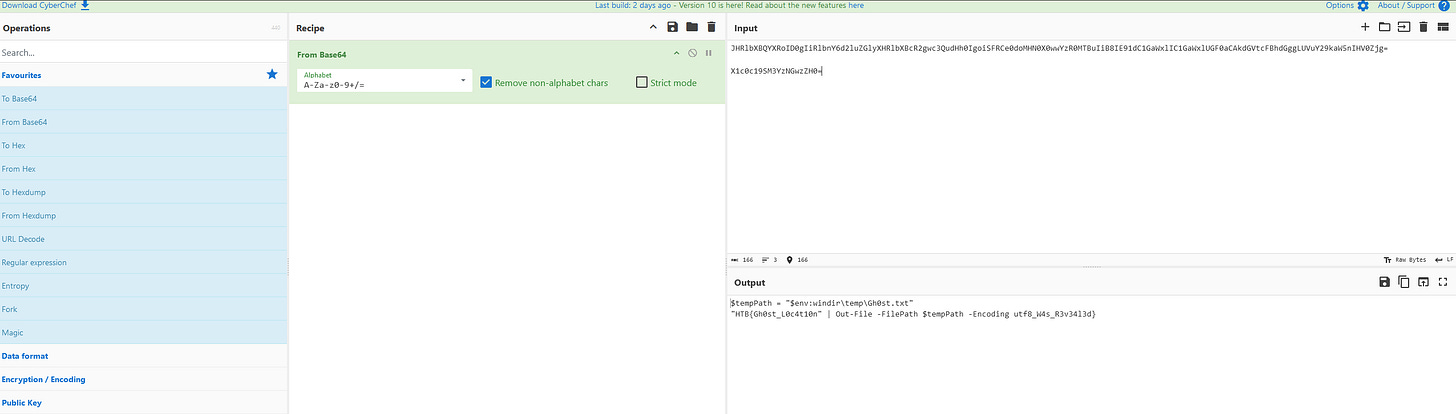
JHRlbXBQYXRoID0gIiRlbnY6d2luZGlyXHRlbXBcR2gwc3QudHh0IgoiSFRCe0doMHN0X0wwYzR0MTBuIiB8IE91dC1GaWxlIC1GaWxlUGF0aCAkdGVtcFBhdGggLUVuY29kaW5nIHV0Zjg=
7. Decode the First Script: Using CyberChef, decode this base64 content to reveal further details.
8. Locate the Second Script: The logs also point to another script at the path:
- `C:\Users\usr01\AppData\Local\Temp\3MZvgfcEiT.ps1`
- The content here is also base64 encoded:
X1c0c19SM3YzNGwzZH0=
9. Decode the Second Script: Decode this base64 content in CyberChef to retrieve the flag.
10. Flag Retrieval: After decoding, the flag contents are revealed.
This methodical approach allows us to use various forensic tools and decode base64 scripts to uncover hidden information in the logs and ultimately find the flag.