Foggy Intrusion CTF Write-Up:
1. PCAP Discovery: We start with a packet capture (PCAP) file and open it in Wireshark. For safety and flexibility, we save it as a raw PCAP.
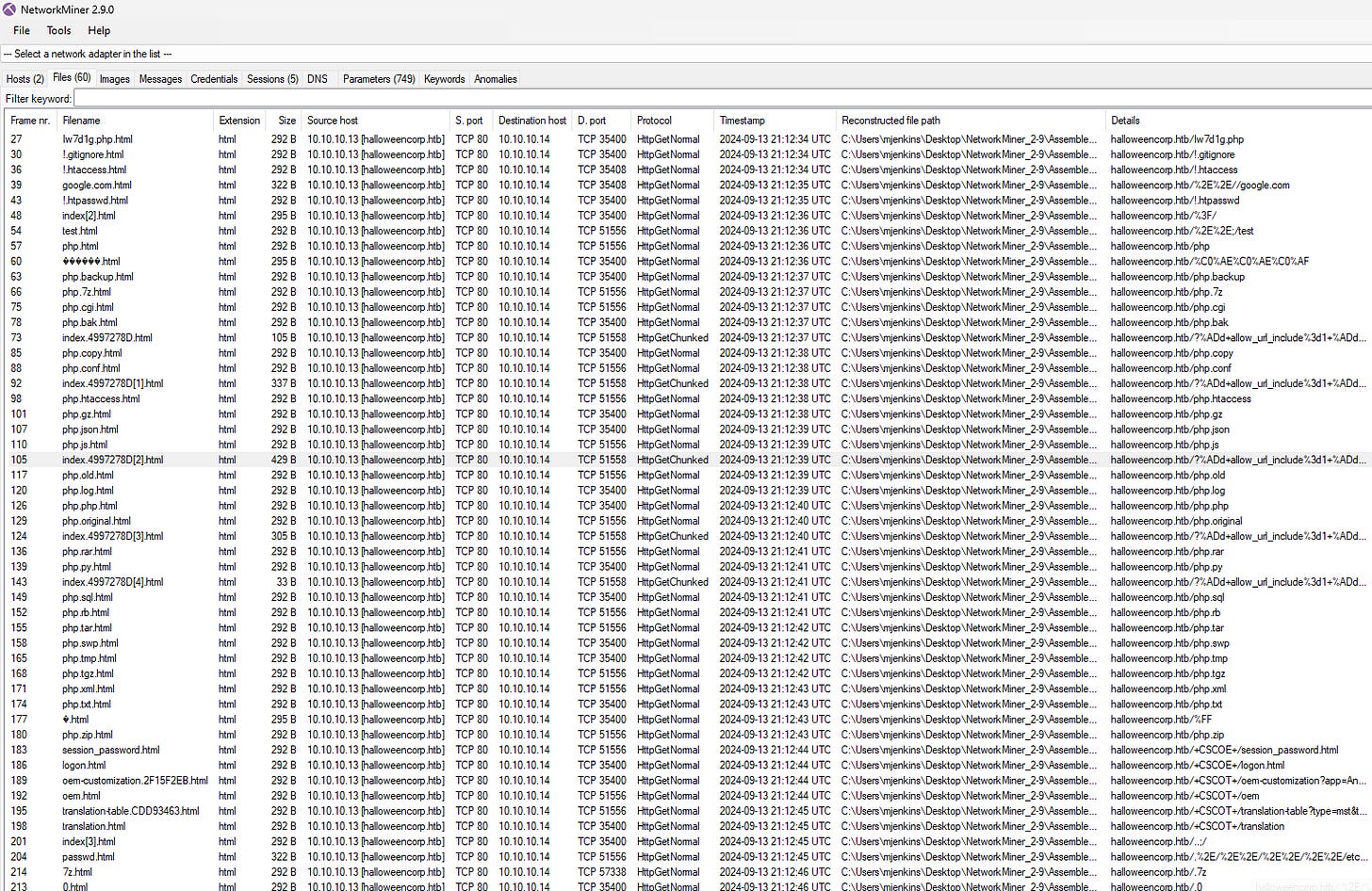
2. Initial Exploration with NetworkMiner: Switching to NetworkMiner, we analyze the PCAP. There are **2 hosts, 60 files, and 5 sessions**—and a lot of PHP traffic stands out. Among the traffic, some files appear related to passwords. Suspicious!
3. Pivot Back to Wireshark: Intrigued, we dive back into Wireshark to inspect individual conversations and search for specific HTTP response codes, particularly **302 Found** and **200 OK**.
4. Follow the HTTP Stream: Right-clicking on an HTTP/1.1 **302 Found** response, we follow the HTTP stream, hoping to uncover more clues.
5. Uncovering Encoded Data: Further investigation reveals POST requests containing PHP shell code running PowerShell, which seems to be encoding data in base64.
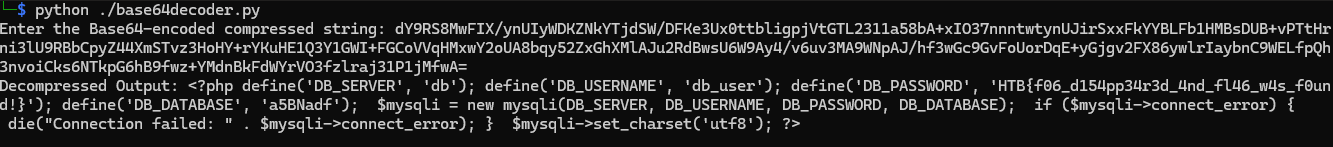
6. Decoding the Obfuscation: The responses include compressed base64 strings. To decode this, we need a Python script capable of decompressing and converting this base64 data into readable text.
7. Extracting the Flag: Running our Python program across all the base64 responses, we finally uncover the hidden flag!
---
This step-by-step process involves analyzing network traffic and decoding obfuscated data, highlighting the power of network forensics in capturing hidden information.