Challenge Description:
There is a rumor that aliens have developed a persistence mechanism that is difficult to detect. After investigating her compromised Linux server, Pandora found a possible sample of this mechanism. The objective is to analyze the provided files and discover how persistence is installed, ultimately revealing the flag.
Steps to Solve:
Download and Extract Files:
Start by downloading the provided challenge files and extract the contents.
Analyze the File:
Open a terminal and navigate to the directory where the file persistence.sh resides.
Run the following command:
file persistence.shThis command will identify the type of file. The result should indicate that it is a shell script.
Read the File Contents:
Use cat or strings to print the contents of the script to the terminal:
cat persistence.sh
or
strings persistence.shNote the base64-encoded data present within the script.
Extract and Copy the Base64 Data:
Identify the base64-encoded string. This string is typically large and encoded to hide the actual payload.
Copy the entire base64 string.
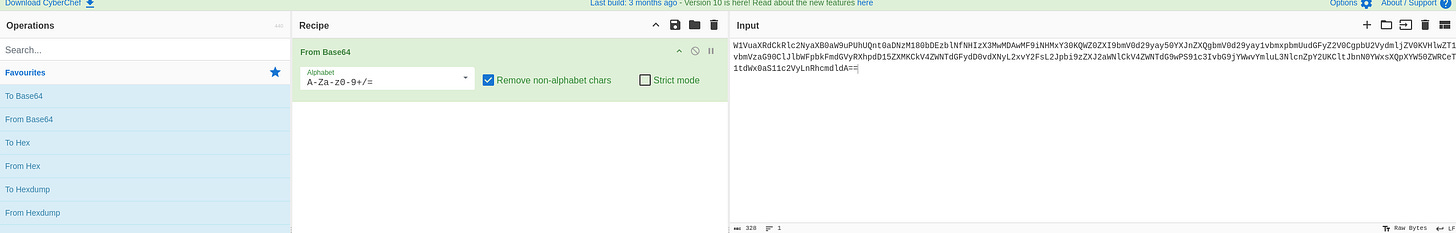
Decode the Base64 Data in CyberChef:
Open CyberChef in your browser.
Select the operation "From Base64."
Paste the copied base64 data into the input section.
Ensure "Remove non-alphabet chars" is checked (to clean up any formatting).
Run the operation by clicking the "Bake!" button.
Review the Decoded Output:
The output of the decoded base64 data should reveal the contents, which may contain important information such as:
The persistence mechanism (e.g., a backdoor command, cron job, or system service).
The flag for the challenge.
Expected Result:
The decoded output in CyberChef should display the flag in plain text, confirming the solution.
Command Reference:
# Step 1: Verify the file type
file persistence.sh
# Step 2: Print contents of the file
cat persistence.sh
# Step 3: Decode using CyberChef (copy the base64 string)
This systematic approach ensures that you decode and understand how the persistence mechanism works while obtaining the challenge flag.