Sherlock Scenario
Situation: The customer has been alerted about concerning reports indicating a potential breach of their database, with information allegedly circulating on the darknet market. As the Incident Responder, the task is to conduct an investigation into an email received by an employee, comprehend its implications, and uncover connections to the data breach. The focus is to examine the provided artifacts to identify significant events on the victim's workstation.
Note: The first thing that I like to do when I get these KAPE target outputs is to run it through a KAPE module such as !EZParser using the command: ./kape.exe --msource "C:\Users\Username\Desktop\wb-ws-01" --module !EZParser --mdest "C:\Users\Username\Desktop\KOUT\" . This will be useful to us in the future as we continue working through the tasks.
1. The victim received an email from an unidentified sender. What email address was used for the suspicious email?
Method: The investigation starts by identifying the Outlook .ost file:
Location:
C:\Users\Username\Desktop\wb-ws-01\C\Users\ash.williams\AppData\Local\Microsoft\OutlookTool Used: PSTWalker
Steps:
Open the .ost file in PSTWalker.
Navigate to the Inbox folder and identify the suspicious email.
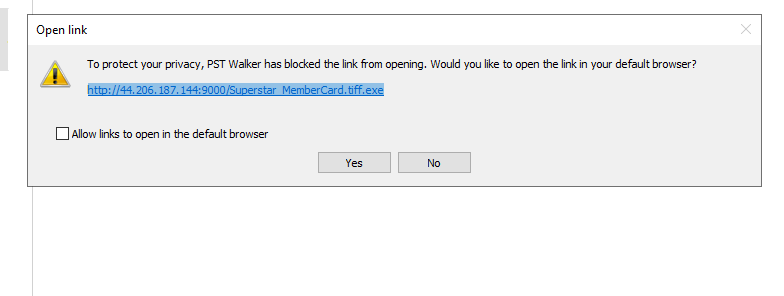
2. It appears there’s a link within the email. Can you provide the complete URL where the malicious binary file was hosted?
Method:
Inspect the body of the email within PSTWalker to find the complete URL.
3. The threat actor managed to identify the victim's AWS credentials. From which file type did the threat actor extract these credentials?
Method:
Search through the extracted email attachments and associated files.
The AWS credentials were identified in an attachment file.
4. Provide the actual IAM credentials of the victim found within the artifacts.
Method:
Continue browsing through PSTWalker and identify the specific IAM email.
Extract the IAM credentials from the email body.
5. When (UTC) was the malicious binary activated on the victim’s workstation?
Method:
Open the PECmd Timeline CSV using Timeline Explorer.
Filter for:
Superstar_MemberCard.tiff.exeResult: Note the execution time of the binary in UTC.
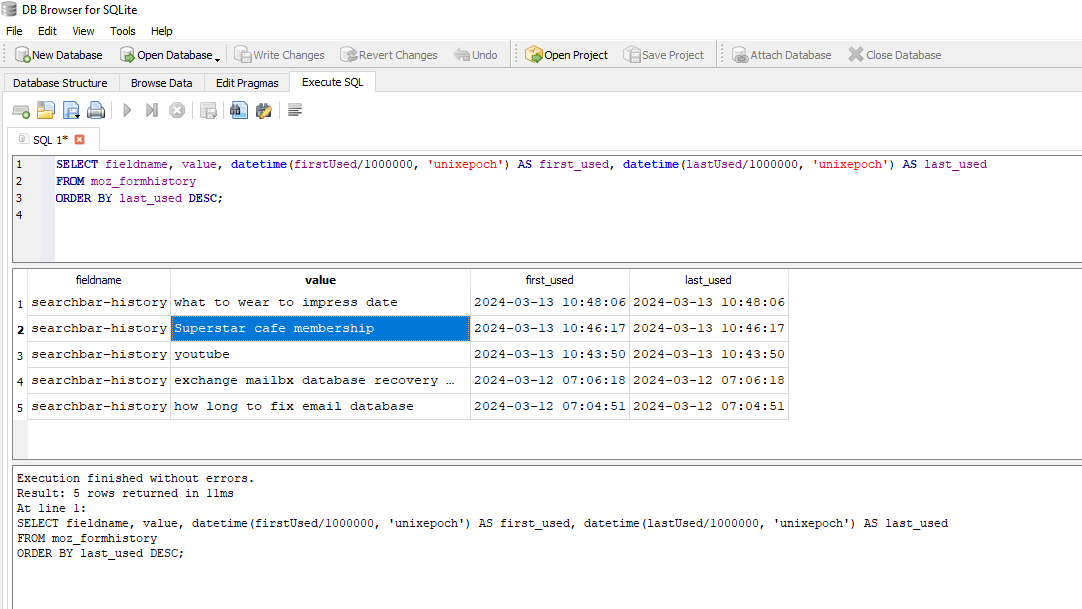
6. Following the download and execution of the binary file, the victim attempted to search for specific keywords on the internet. What were those keywords?
Method:
Open the browser history database using DB Browser for SQLite.
Run the following SQL query:
SELECT url, title, datetime(last_visit_time/1000000-11644473600, 'unixepoch') AS visit_time
FROM urls
WHERE url LIKE '%search%' OR title LIKE '%search%';Check for search-related keywords in the query results.
7. At what time (UTC) did the binary successfully send an identical malicious email from the victim’s machine to all the contacts?
Method:
Open the Sent Mail folder in PSTWalker.
Right-click the email and choose MAPI Properties.
Check the PR_CLIENT_SUBMIT_TIME property and convert it to UTC.
Compare the time to the binary’s execution time to ensure consistency.
8. How many recipients were targeted by the distribution of the said email excluding the victim’s email account?
Method:
In PSTWalker, check the MAPI properties of the email.
Count the recipients listed in the To and BCC fields.
9. Which legitimate program was utilized to obtain details regarding the domain controller?
Method:
Open Timeline Explorer and filter for the process:
Superstar_MemberCard.tiff.exeCheck the Payload section for related commands such as nltest.exe, whoami, or net.exe.
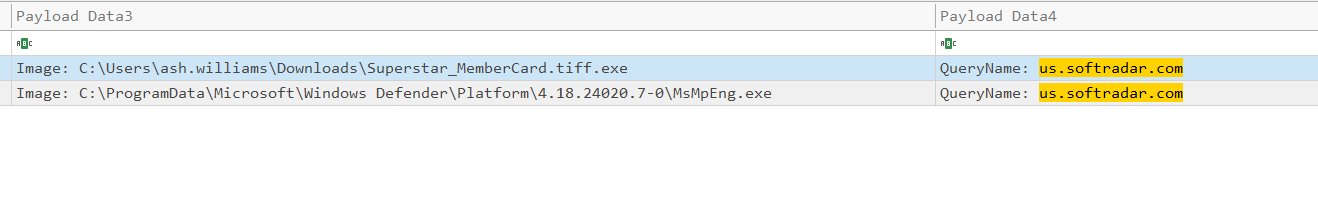
10. Specify the domain (including sub-domain if applicable) that was used to download the tool for exfiltration.
Method:
Open Timeline Explorer and filter the Map Description for:
DNSEventIdentify the domains queried that led to the download.
11. The threat actor attempted to conceal the tool to elude suspicion. Can you specify the name of the folder used to store and hide the file transfer program?
Method:
In Timeline Explorer, filter for:
Superstar_MemberCard.tiff.exeLocate the Parent Directory or folder path where the executable resides.
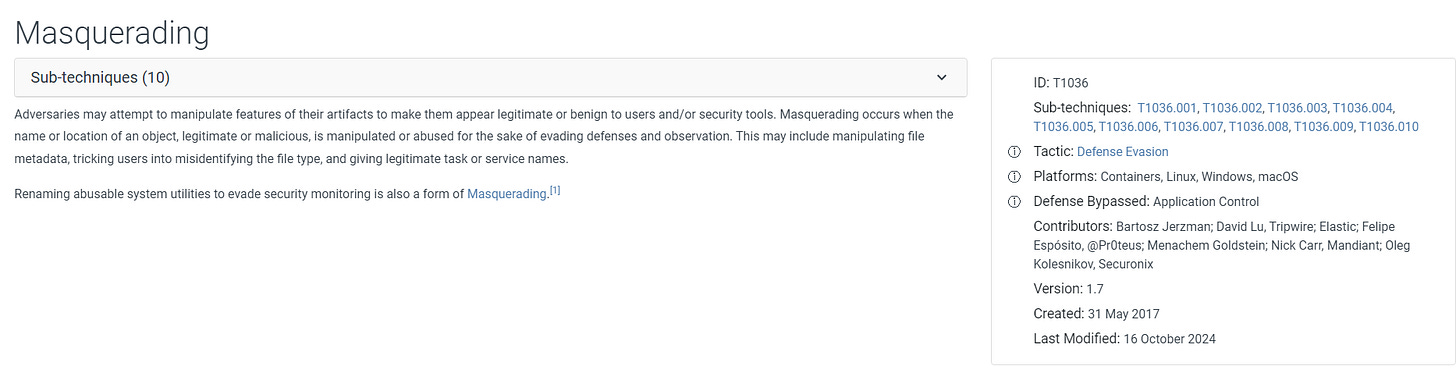
12. Under which MITRE ATT&CK technique does the action described in question #11 fall?
Method:
Conduct a quick online search for the action (e.g., file concealment, renaming, or hiding directories).
The likely MITRE ATT&CK technique is T1564.001 - Hidden Files and Directories.
13. Can you determine the minimum number of files that were compressed before they were extracted?
Method:
Note: Timeline Explorer may not always show all files.
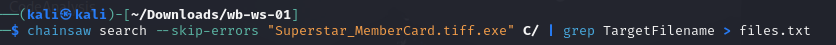
Use Chainsaw in Kali Linux:
./chainsaw search --skip-errors "Superstar_MemberCard.tiff.exe" C/ | grep TargetFilename > files.txt
cat files.txt | grep -vE ".exe|.ps1|tiff|zip|HelpDesk" | grep ".*\..*" | sort | uniqCheck for the number of unique file paths extracted from the compressed file.
14. To exfiltrate data from the victim's workstation, the binary executed a command. Can you provide the complete command used for this action?
Method:
In Timeline Explorer, search for:
winscp.exeLocate the ParentCommandLine field in the Payload section to find the complete exfiltration command.