1. Find any suspicious files under Bingle Jollybeard User Directory and get back to us with the full file name.
The KAPE extraction reveals suspicious files under the C folder. Navigating to Bingle Jollybeard's Documents folder, we find a christmas_slab.pdf shortcut as a potential malicious file.
Tip: take the C folder we were provided and run it through KAPE again, this time running KAPE modules against it. This will speed things up.
Command to Run KAPE:
kape.exe --msource "c:\Users\UserName\Desktop\TRIAGE-L3-BELLS" --module EZParser --mdest "c:\temp" --trace --debug
2. Using the malicious file sent as part of phishing, the attacker abused a legitimate binary to download and execute a C&C stager. What is the full command used to download and execute the C&C Binary?
The Shortcut tab in the christmas_slab.pdf properties reveals the full command used for downloading and executing the C&C Binary.
3. When was this file ran on the system by the victim?
Using PECmd to parse prefetch logs from the C folder in the KAPE output, load the timeline CSV into Timeline Explorer to get the timestamp of execution.
4. What is the MITRE Sub-Technique ID for the technique used in Q1 and Q2?
The phishing attack used a .lnk file masquerading as a .pdf to execute malicious content.
Sub-Technique ID: T1204.002
Description: Malicious File Execution via Shortcut.
5. What was the name of the threat actor's machine used to develop/create the malicious file sent as part of phishing?
Run LECmd to extract metadata from the malicious link file.
Command: LECmd.exe -f "path\to\christmas_slab.pdf.lnk" --csv "path\to\output"
Open the CSV in Timeline Explorer and check the Machine ID field.
6. When did the attacker enumerate the running processes on the system?
Identify commands used to enumerate running processes, such as tasklist.exe, by filtering the prefetch CSV for related activity.
7. After establishing a C&C Channel, the attacker proceeded to abuse another legitimate binary to download an exe file. What is the full URI for this download?
Filter .exe and http in Timeline Explorer to reveal a BITS job downloading a file from an IP address.
8. What is the MITRE ID for the technique used in Q7?
ID: T1197 (BITS Jobs for malicious downloads).
9. In the workshop environment, RDP was only allowed internally. It is suspected that the threat actor stole the VPN configuration file for Bingle Jollybeard, connected to the VPN, and then connected to Bingle's workstation via RDP. When did they first authenticate and successfully connect to Bingle's workstation?
Filter event logs (parsed with EVTCmd and Timeline Explorer) for RDP activity to find the first successful authentication.
10. Any IOCs we find are critical to understanding the scope of the incident. What is the hostname of the attacker's machine making the RDP connection?
Extract the hostname from the username field in the event logs, formatted as ComputerName\UserName.
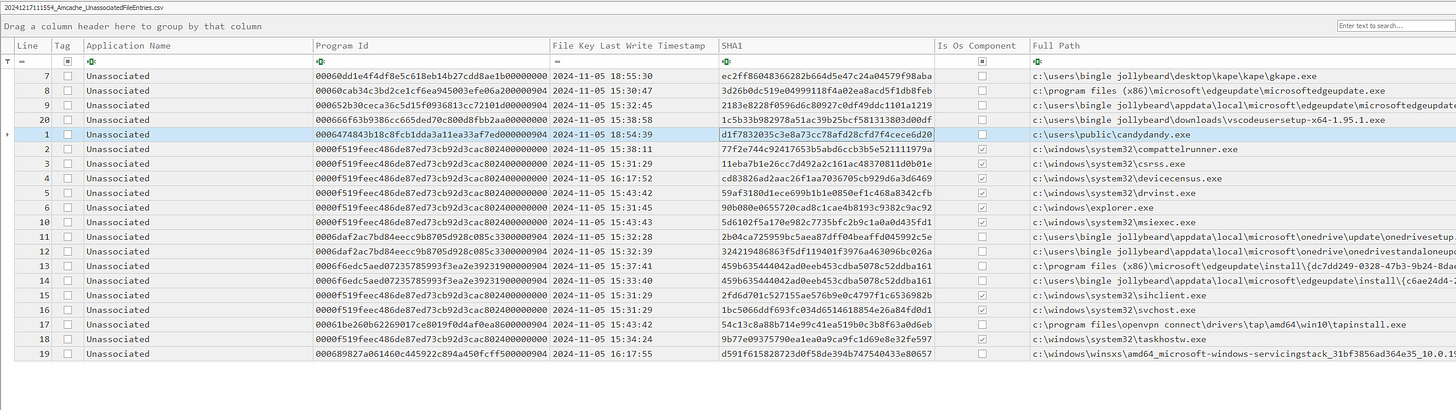
11. What is the MD5 hash of the file downloaded in Q7?
Analyze the Amcache for records of executed binaries on Windows hosts. Run the KAPE modules against the target using the compound module to generate Amcache CSVs.
Load the CSVs into Timeline Explorer to retrieve the SHA1 hash.
Use VirusTotal or a hashing tool to convert the SHA1 to MD5.
12. Determine the total amount of traffic in KBs during the C&C control communication from the stager executable.
Identify the stager executable by checking the target of the malicious PDF link (e.g., christmas-sale.exe).
Filter the SRUM network logs for the stager.
Add up sent and received bytes, dividing by 1000 for KB.
13. As part of persistence, the attacker added a new user account to the workstation and granted them higher privileges. What is the name of this account?
Filter event logs for Event ID 4720, which logs user account creation. Look for the account name.
14. After completely compromising Bingle's workstation, the attacker moved laterally to another system. What is the full username used to log in to the system?
Filter event logs in Timeline Explorer for Event ID 4648. Look for the username: NORTHPOLE-BINGL\Bingle Jollybeard and identify target servers.
15. According to the remote desktop event logs, what time did the attack successfully move laterally?
Search for the keyword "nippy" in the RDP logs to find the timestamp of the successful RDP connection.
16. After moving to the other system, the attacker downloaded an executable from an open directory hosted on their infrastructure. What are the two staging folders named?
Navigate to the folder:
TRIAGE-L3-BELLS\C\Users\Bingle Jollybeard\AppData\Local\Microsoft\Terminal Server Client\Cache.
Reconstruct the cache to bitmap images using bmc-tools.py:
bmc-tools.py -s "Path/To/Cache" -d "rdp_output"
Analyze the BMP files for staging folder names.
17. What is the name of the downloaded executable from the open directory?
Reconstruct and analyze the BMP files (as in Q16). Combine image data, if necessary, to identify the executable name.
18. After downloading the executable from Q17, the attacker utilized the exe to be added as a persistence capability. What is the name they gave to this persistence task?
Correlate the reconstructed images (as in Q16 and Q17) to identify the persistence task's name.
19. Same deal, find and correlate.
Similar process to Q16-Q18. Correlate BMP data to identify related artifacts.
20. Determine the total amount of traffic in KBs during the internal lateral movement, which originated from Bingle's workstation to the other machine in the network.
Check SRUM network logs, filtering for Bingle's username and relevant executables (e.g., mstsc.exe). Add sent and received bytes, dividing by 1000 for KB.