Scenario Overview
In this Sherlock Scenario, a rogue elf—spurred by anger after being left off the Nice List and influenced by Krampus—plans to sabotage Christmas by targeting Santa’s critical S3 data archive. The archive contains sensitive information, such as toy blueprints, production schedules, and the all-important gift list. Your mission: investigate the incident, uncover the rogue elf’s actions, and restore the holiday spirit.
Questions and Solutions
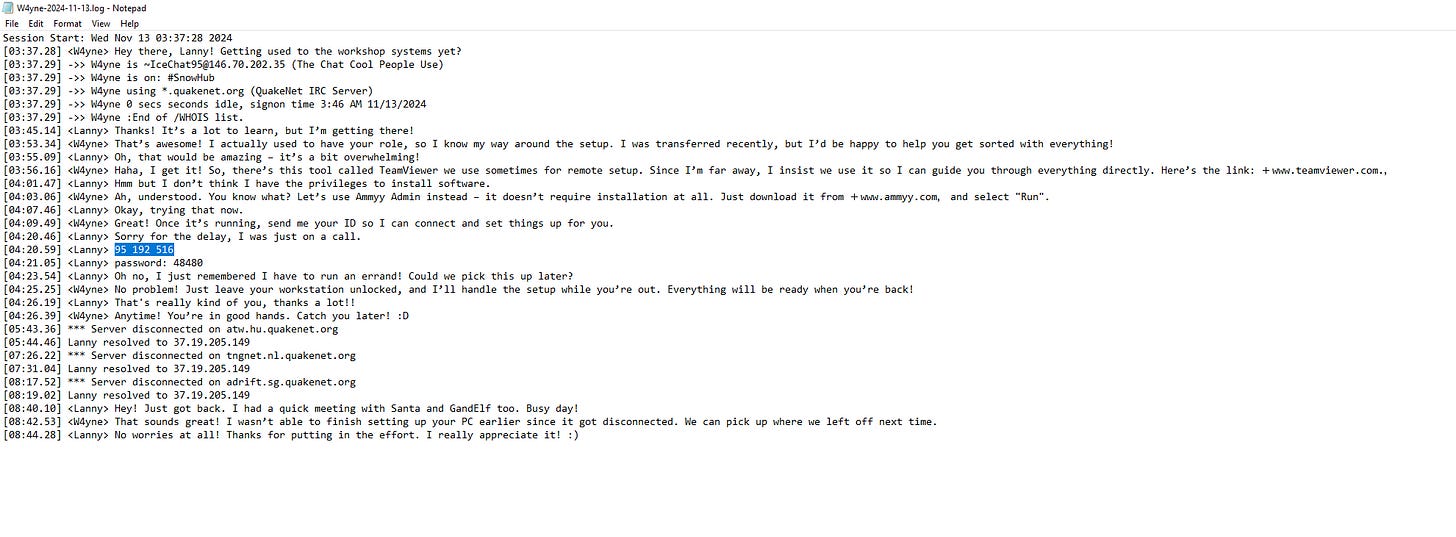
1. The Victim Elf shared credentials that allowed the Rogue Elf to access the workstation. What was the Client ID that was shared?
Approach: Use KAPE with the !EZParse module to parse logs.
Steps:
Analyze the C drive on the NORTHPOLE machine.
Navigate to:
\NORTHPOLE-LUMEN\C\Users\lannyl\AppData\Local\IceChat Networks\IceChat\Logs\irc.quakenet.org\Query.Extract the Client ID from the IRC chat logs.
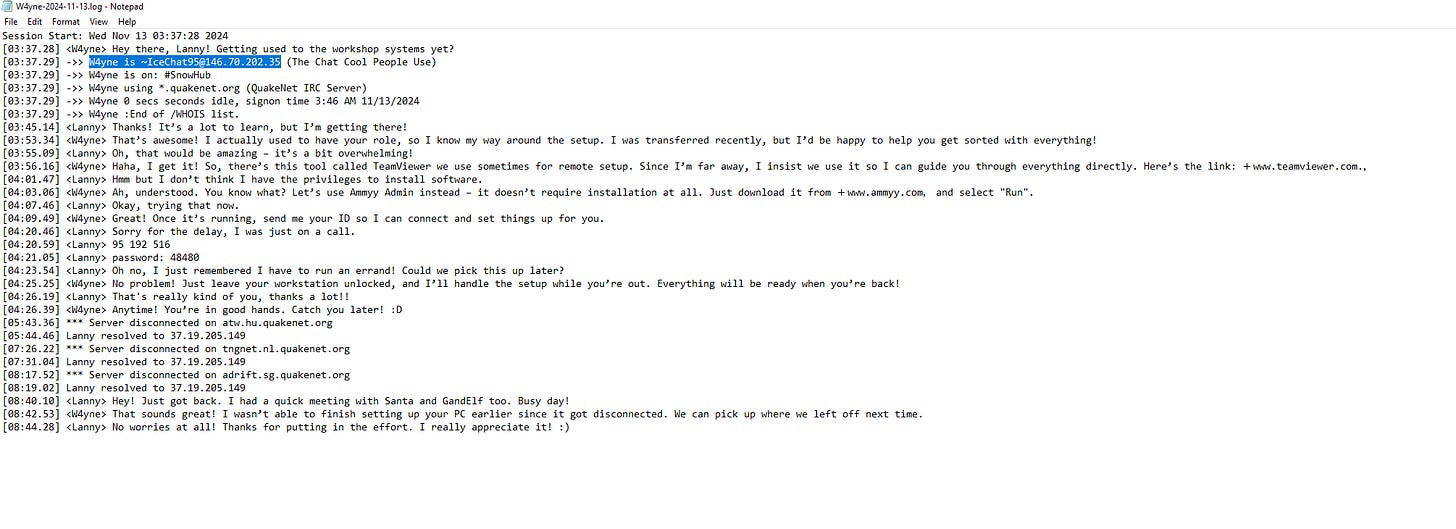
2. What is the IP address of the Rogue Elf used during the attack?
Approach: Locate the IP address in the same IRC log file as Question 1.
3. What is the name of the executable the victim ran to enable remote access to their system?
Approach:
The program is ammyy, a remote control software.
Use Timeline Explorer to inspect Amcache unassociated file entries for related executables.
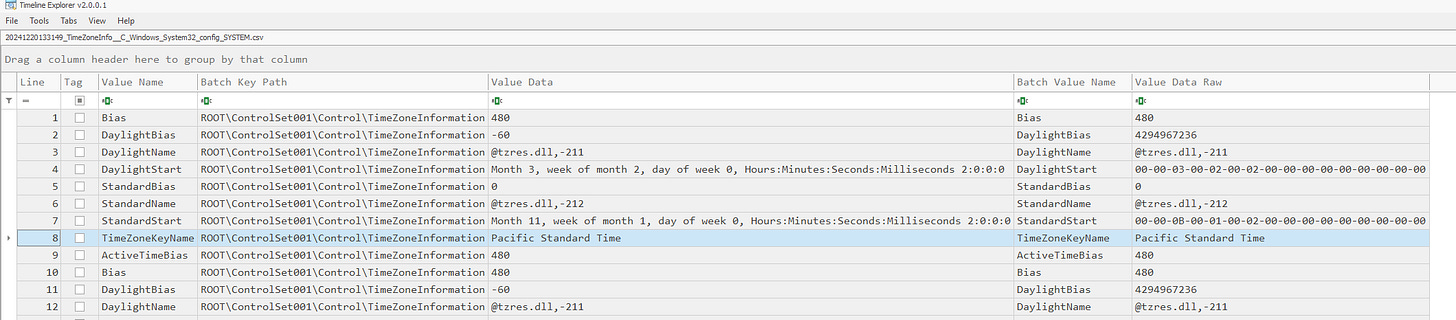
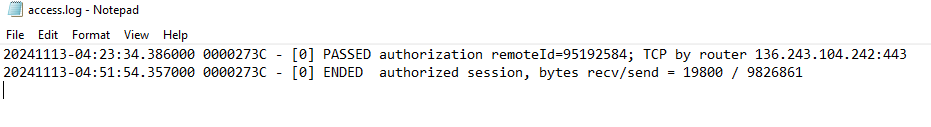
4. What time (UTC) did the Rogue Elf connect to the victim's workstation?
Approach:
Access the Ammyy logs:
\Blizzard\NORTHPOLE-LUMEN\C\ProgramData\Ammyy.Extract the timestamp (local time).
Use KAPE logs and Timeline Explorer to identify system time settings in the registry hive.
Convert the timestamp to UTC.
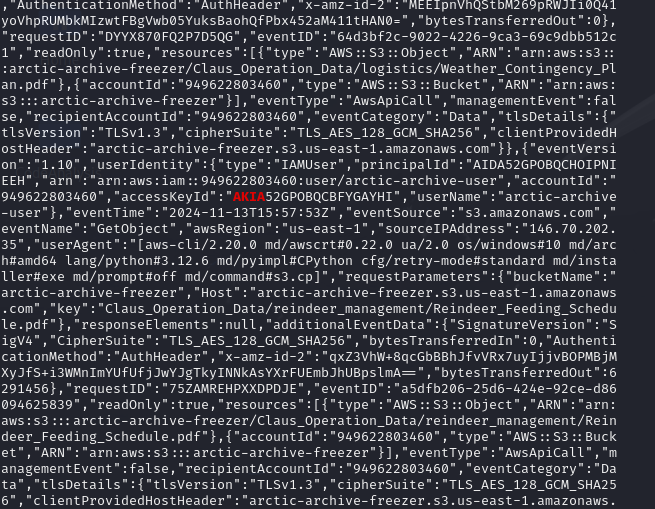
5. The Rogue Elf compromised an AWS Access Key. What is the AWS Access Key ID obtained from the victim's workstation?
Approach:
Transfer logs to Kali Linux for easier handling of .gz files.
Search the logs for AWS credentials using tools like zcat or grep.
6. Which S3 bucket did the Rogue Elf target during the incident?
Approach: Refer to the logs or screenshots from Question 5 to identify the targeted bucket.
7. Within the targeted S3 bucket, what is the name of the main directory where the files were stored?
Approach: The answer is also in the logs or screenshots from Question 5.
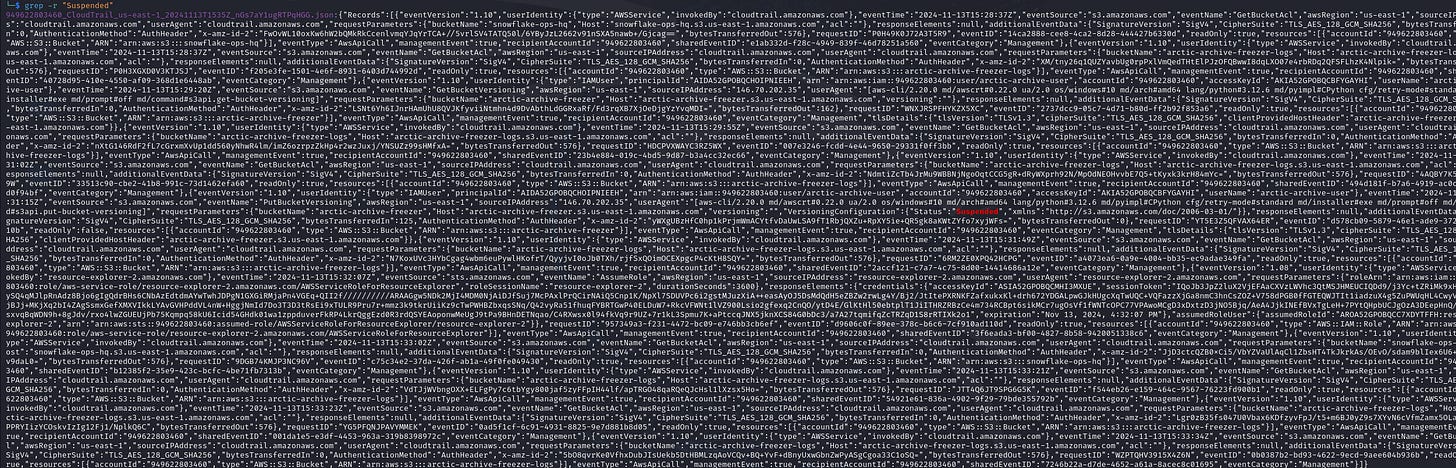
8. What time (UTC) did the Rogue Elf disable versioning for the S3 bucket?
Approach:
Filter logs using keywords PutBucketVersioning and Suspended.
9. What is the MITRE ATT&CK Technique ID associated with the method used in Question 8?
Answer: T1490 – Inhibit System Recovery
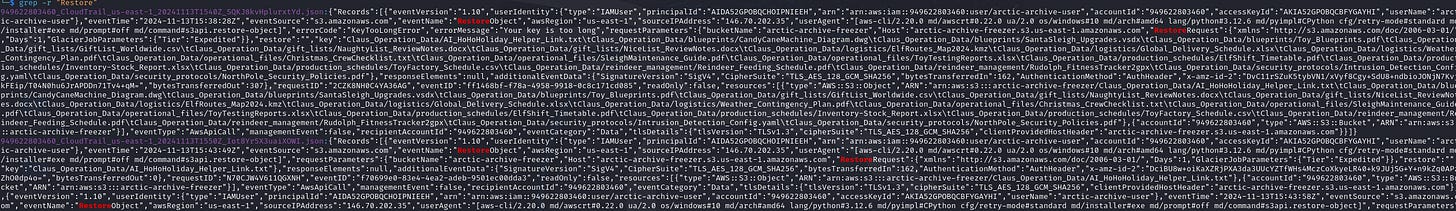
10. What time (UTC) was the first restore operation successfully initiated for the S3 objects?
Approach: Search logs for restore operations.
Steps: If the first record contains an error, check the next successful operation.
11. Which retrieval option did the Rogue Elf use to restore the S3 objects?
Answer: Expedited
Found in the RestoreRequest logs under GlacierJobParameters.
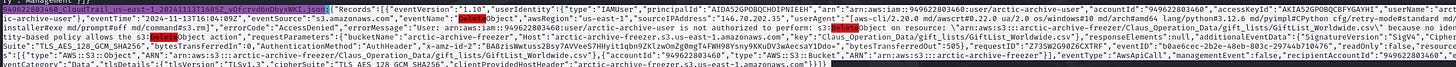
12. What is the filename of the S3 object that the Rogue Elf attempted to delete?
Approach:
Search for DeleteObject events in the logs.
Extract the filename associated with the key.
13. What is the size (MB) of the S3 object that the Rogue Elf targeted in Question 12?
Approach: Calculate the size in MB.
Steps:
Use this command:
find ./ -type f -name "*.json" -exec cat {} + | jq '.Records[] | select(.eventName == "GetObject") | select(.requestParameters.key == "Claus_Operation_Data/gift_lists/GiftList_Worldwide.csv") | .additionalEventData.bytesTransferredOut'Divide the total bytes by 1024 * 1024 to convert to MB.
14. The Rogue Elf uploaded corrupted files to the S3 bucket. What time (UTC) was the first object replaced during the attack?
Approach:
Search for PutObject events targeting S3 objects.
Use this command:
find ./us-east-1 -type f -name "*.json" -exec cat {} + | jq 'select(.eventName == "PutObject" and .requestParameters.key == "Claus_Operation_Data/gift_lists/GiftList_Worldwide.csv") | {eventTime, eventName, requestParameters}'Find the earliest timestamp.
15. What storage class was used for the S3 objects to mimic the original settings and avoid suspicion?
Approach: Look for the StorageClass key in the logs.
Answer: Extract the value for the StorageClass key, which indicates the storage settings.
This write-up utilizes tools such as KAPE, Timeline Explorer, and Kali Linux for efficient log analysis, employing commands like find, cat, and jq to parse and filter JSON data. By methodically investigating logs, artifacts, and metadata, the rogue elf’s actions were uncovered step-by-step, ensuring Christmas was saved.