Hack The Box Sherlock Challenge: Recollection
Scenario Overview
The junior security team suspects that an old and insecure operating system has been compromised. A memory dump was retrieved, and our job is to analyze it to uncover evidence of an attack and its details.
Step-by-Step Analysis
1. Finding the Operating System
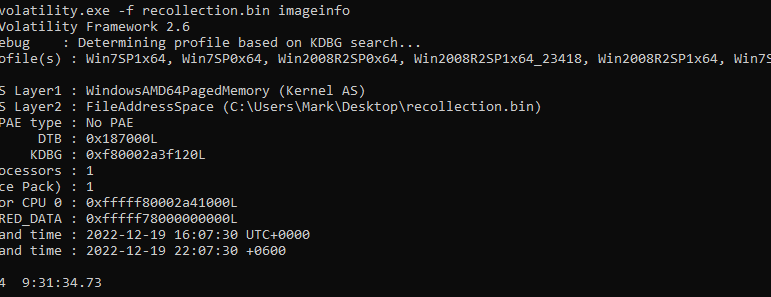
Run Volatility with the imageinfo command to gather metadata about the memory dump, including the operating system version and architecture:
volatility.exe -f recollection.bin imageinfo
2. Determining the Memory Dump Creation Date
Analyze the imageinfo output to locate the timestamp indicating when the memory dump was created.
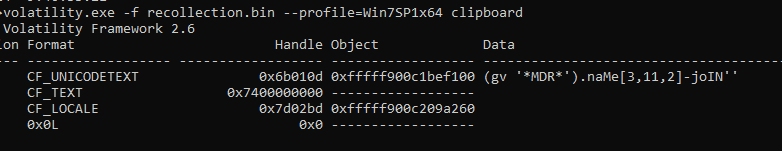
3. Extracting the Obfuscated PowerShell Command
Inspect the clipboard content using Volatility to locate any copied commands:
volatility.exe -f recollection.bin --profile=Win7SP1x64 clipboard
4. Identifying the Cmdlet Name
Analyze the extracted PowerShell command from the clipboard data to determine the cmdlet used.
5. Extracting the Full CMD Command
Retrieve executed commands from the command prompt history using Volatility:
volatility.exe -f recollection.bin --profile=Win7SP1x64 cmdscan
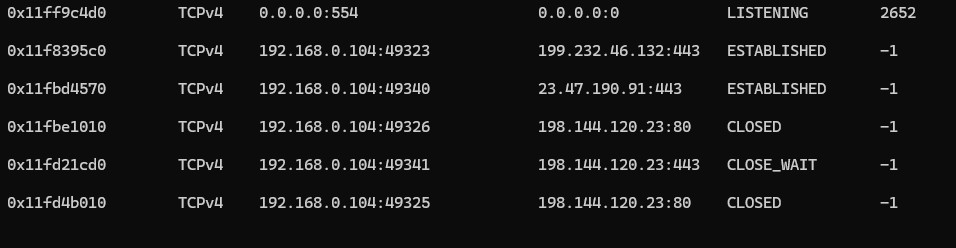
6. Verifying File Exfiltration
Analyze the network activity to check for successful connections to the exfiltration destination:
volatility.exe -f recollection.bin --profile=Win7SP1x64 netscan
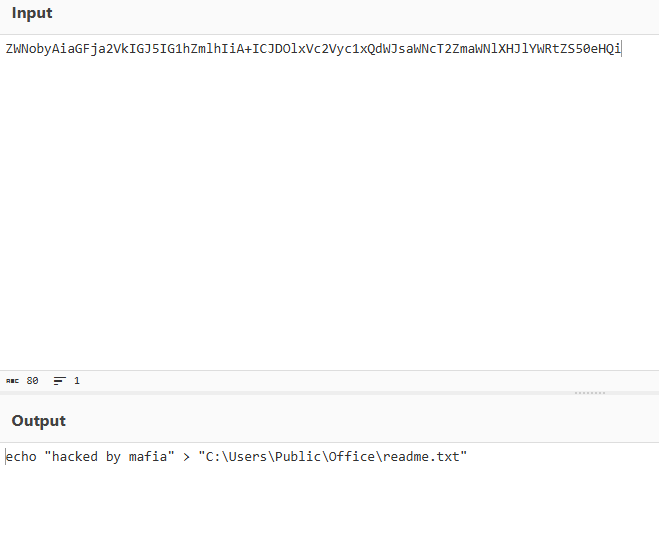
7. Locating the Readme File Path
Deobfuscate the PowerShell command found in the CMD scan using a tool like CyberChef to reveal the full file path.
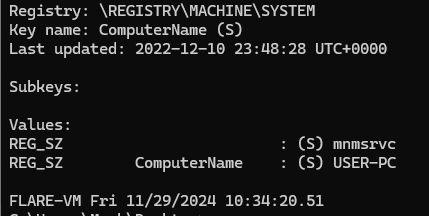
8. Extracting the Host Name
Query the system’s registry keys to retrieve the hostname:
volatility.exe -f recollection.bin --profile=Win7SP1x64 printkey -K "ControlSet001\Control\ComputerName\ComputerName"
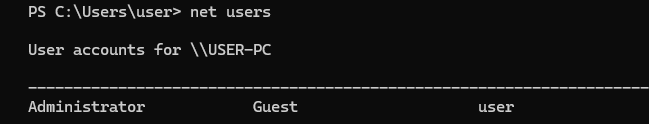
9. Counting User Accounts
Use the strings command to search for user account data and locate evidence of user enumeration:
strings recollection.bin | findstr /i "C:\Users"
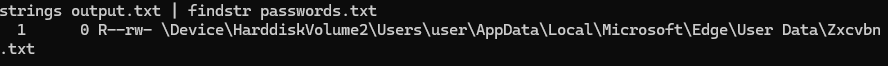
10. Finding the Full Path of the Password File
Scan for files in the memory dump, then search for the specific file name:
volatility.exe -f recollection.bin --profile=Win7SP1x64 filescan > output.txt
strings output.txt | findstr passwords.txt
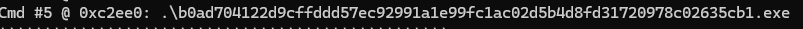
11. Identifying the Malicious Executable
Review the CMD command history to identify a hash-based executable name and locate its presence in the memory.
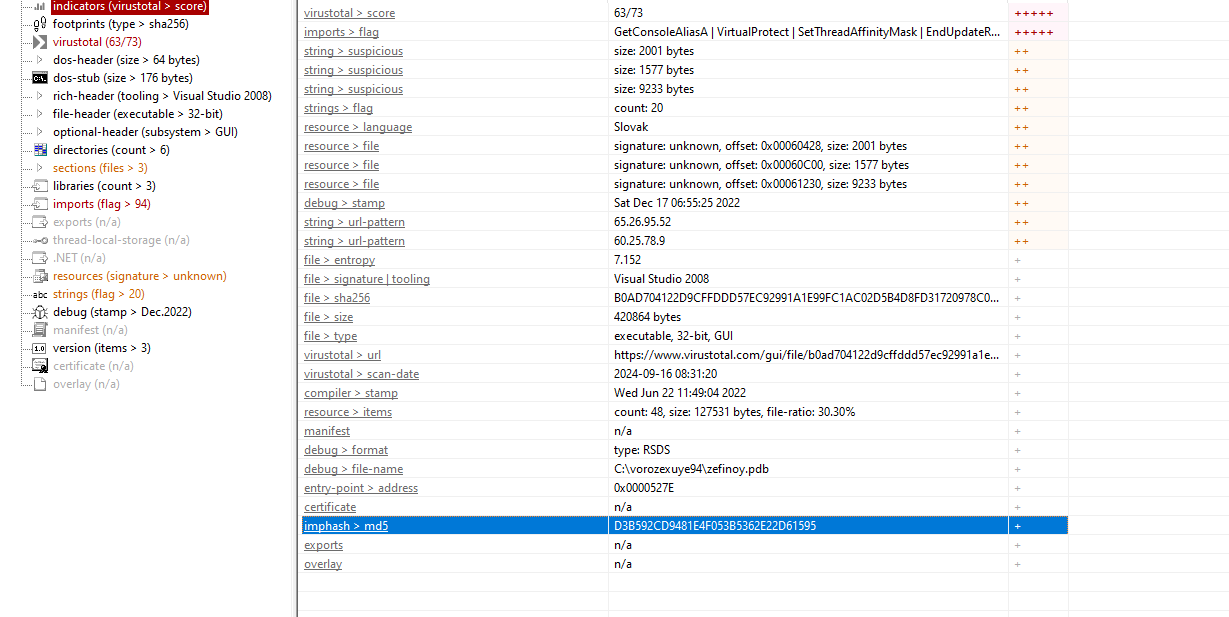
12. Extracting the Imphash of the Malicious File
Locate the executable in memory, dump it using Volatility, and analyze it using a tool like PEStudio:
volatility.exe -f recollection.bin --profile=Win7SP1x64 filescan | findstr "<hash_value>"
volatility.exe -f recollection.bin --profile=Win7SP1x64 dumpfiles -Q <memory_address> -D ./ScanMe
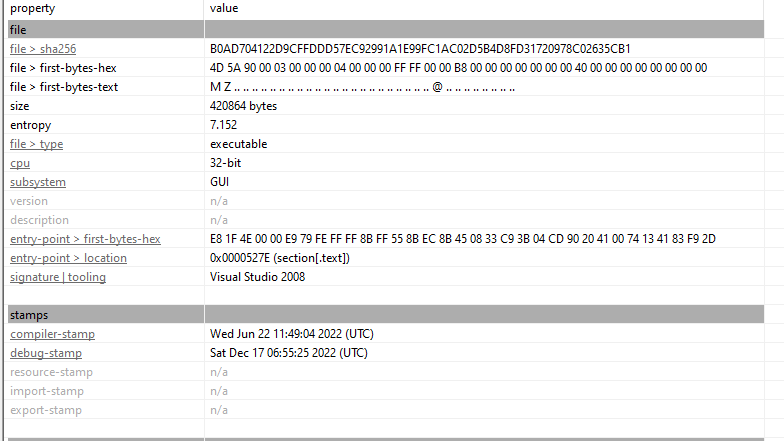
13. Finding the File Creation Date
Analyze the dumped executable with PEStudio or a similar tool to retrieve the creation date.
14. Locating the Machine’s Local IP
Use Volatility to examine the network activity and identify the local IP:
volatility.exe -f recollection.bin --profile=Win7SP1x64 netscan
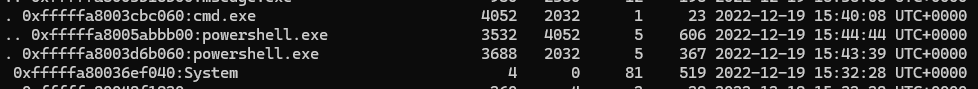
15. Finding the Parent Process of PowerShell
Analyze the process tree in Volatility to locate the parent process:
volatility.exe -f recollection.bin --profile=Win7SP1x64 pstree
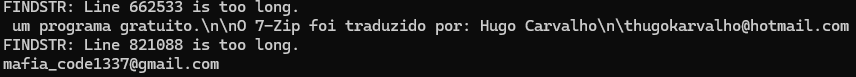
16. Extracting the Attacker’s Email Address
Search the memory dump for email addresses using strings:
strings recollection.bin | findstr /i "@gmail.com @yahoo.com @outlook.com @hotmail.com"
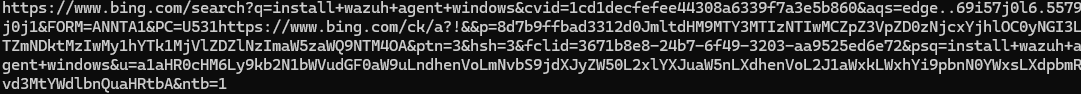
17. Identifying the SIEM Solution Searched by the Victim
Scan for browser history in memory, locate the appropriate history file, and extract it:
volatility.exe -f recollection.bin --profile=Win7SP1x64 filescan | findstr /i "History"
strings <extracted_history_file>
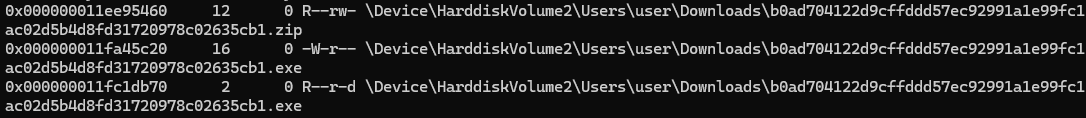
18. Finding the Malicious File Downloaded by the Victim
Search for files in the Downloads folder and locate the malicious file with the typo in its name:
volatility.exe -f recollection.bin --profile=Win7SP1x64 filescan | findstr /i "Downloads"
Conclusion
By following these steps, we can systematically analyze the memory dump to uncover critical evidence of the attacker’s actions and understand the scope of the compromise. This challenge demonstrates the power of memory forensics tools like Volatility for in-depth incident analysis.