Challenge Description
In the race for Vitalium on Mars, the villainous Board of Arodor resorted to desperate measures, needing funds for their mining attempts. They devised a botnet specifically crafted to mine cryptocurrency covertly. A sample of Arodor's miner's installer was discovered on our server. Recognizing the gravity of the situation, a thorough investigation was launched to unravel the inner workings of the installation mechanism. This discovery served as a turning point, revealing the extent of Arodor's desperation. However, the battle for Vitalium continued, urging the team to remain vigilant and enhance cyber defenses.
Steps to Solve the Challenge
1. Download the Files
The first step involved downloading the provided challenge files.
2. Unzip the Files
After downloading, the files were extracted using the unzip command.
unzip challenge_files.zip
3. Analyzing the miner_installer.sh Script
A file command was used to determine the type of the miner_installer.sh file.
file miner_installer.sh
The output indicated that it was a shell script.
4. Extracting Contents Using strings or cat
To reveal the contents of the shell script, the following command was used:
strings miner_installer.sh
Alternatively:
cat miner_installer.sh
Upon inspection, the script contained several encoded strings and sections related to the installation and obfuscation mechanism.
5. Identifying Points of Interest
The script was fairly lengthy and contained several encoded or encrypted components.
Noteworthy points included:
Indicators of Compromise (IoCs) such as file paths, URLs, and potential registry keys.
Base64 encoded strings, likely containing instructions or parts of the flag.
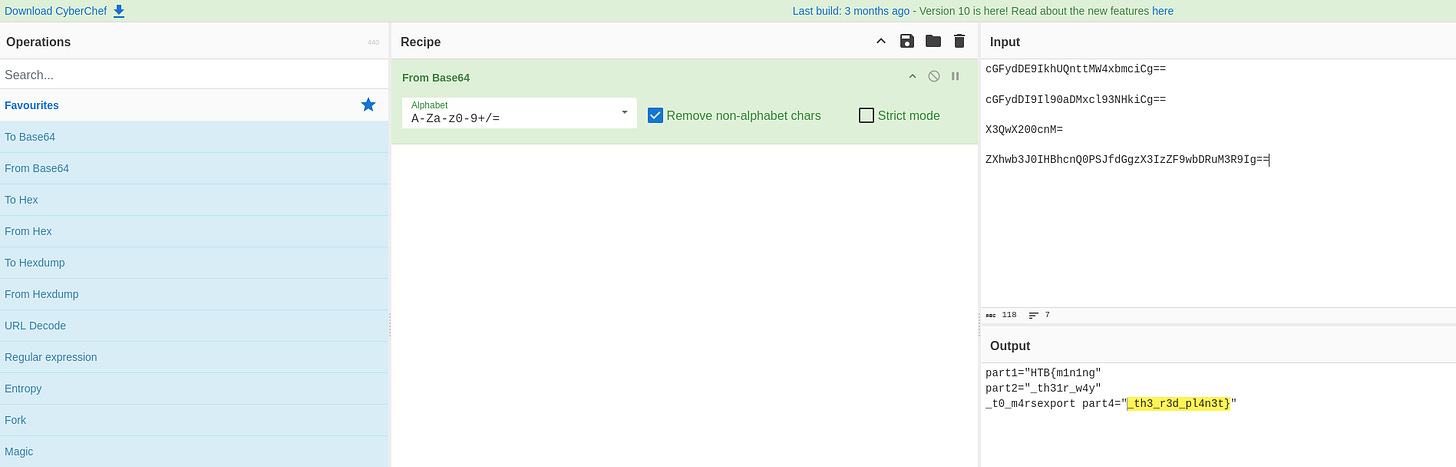
6. Base64 Encoded Strings
Several Base64 encoded strings were extracted from the script, including:
c6FydDE9IkhUQnttMW4xbmNcCg==
c6FydDI9I190aD3lc93NHkicg==
X3QwK200cnM=
ZXhwb3J0IHBhcnQ9PSJfdGgzX3IzZF9wbDRuM3R9Ig==
7. Decoding the Strings with CyberChef
Each Base64 string was decoded using CyberChef:
Open CyberChef and paste the Base64 string in the input section.
Select the From Base64 operation.
Decode the string to obtain its plaintext value.
8. Assembling the Flag
Reconstruct the decoded base64 to get the flag, put in logical order.
Conclusion
The challenge demonstrated how malicious actors can obfuscate installation mechanisms to perform cryptocurrency mining covertly. By carefully dissecting the script, identifying encoded strings, and using tools like CyberChef to decode the strings, the entire flag was successfully retrieved. Additionally, this challenge emphasized the importance of identifying Indicators of Compromise (IoCs) to enhance network defenses.