Scenario
Alonzo noticed suspicious files on his computer and alerted the newly established SOC Team. The team suspects a Kerberoasting attack within the network. Your role is to validate this suspicion by analyzing the provided evidence.
You are provided with:
Security Logs from the Domain Controller
PowerShell-Operational Logs from the affected workstation
Prefetch Files from the affected workstation
Questions and Analysis
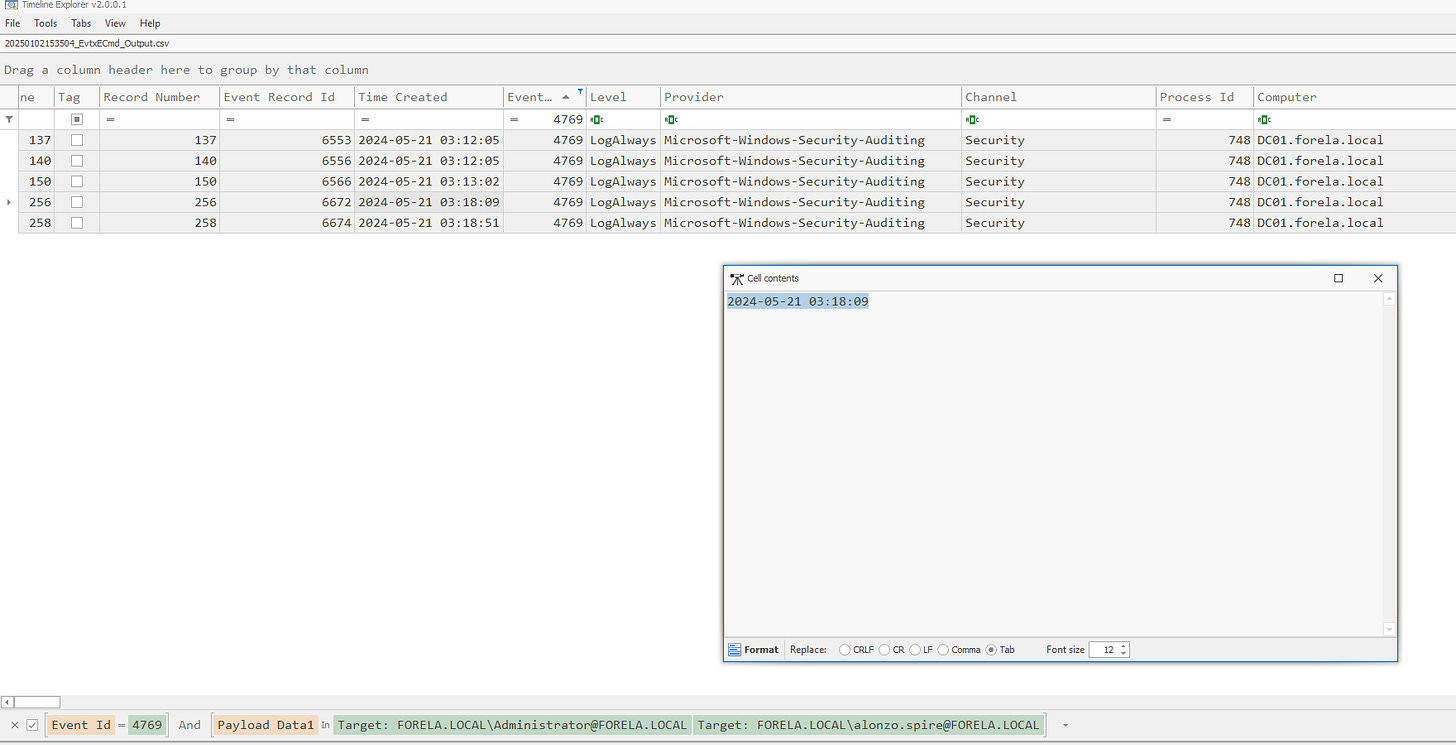
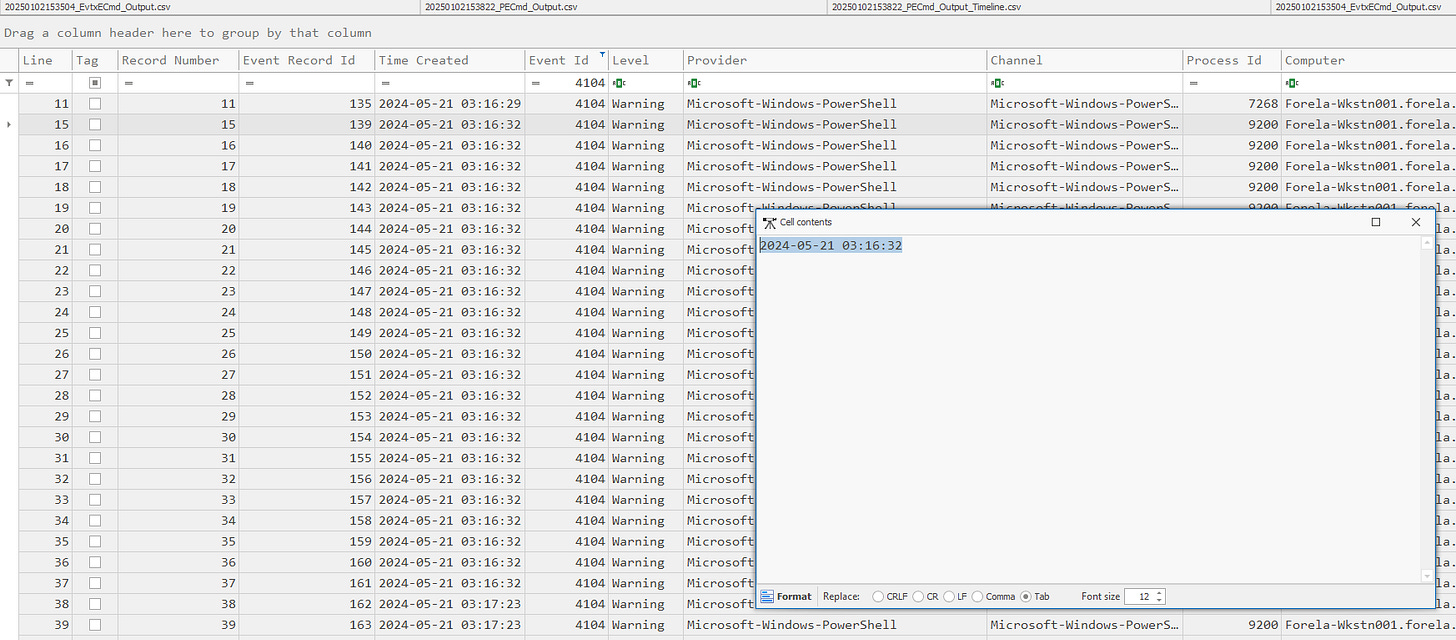
1. Confirming the Date and Time of the Kerberoasting Activity
Approach:
Use Eric Zimmerman’s tool EvtxECmd to parse the event logs efficiently.
Load the parsed logs into the Timeline Viewer for analysis.
Use the following KAPE command to process triage files for faster insights:
./kape.exe --msource "C:\Users\Username\Desktop\Triage\Workstation\2024-05-21T033012_triage_asset" --module !EZParser --mdest "C:\Users\Username\Desktop\"Filter logs for Event ID 4769 (Kerberos Service Ticket Operations) and focus on user accounts that are not machine accounts. Look for RC4 encryption, as it is often targeted due to its vulnerability to cracking.
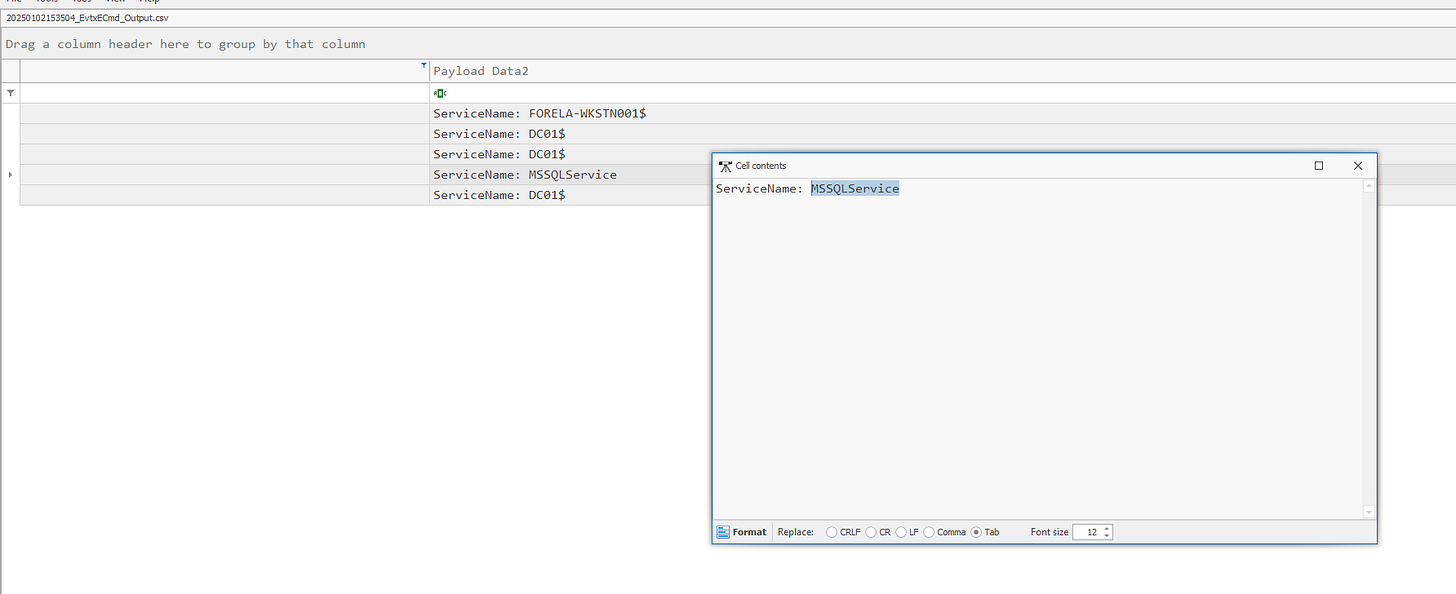
2. Identifying the Targeted Service Name
Approach:
Use the same filtered logs from Question 1.
Check the Payload Data2 field to identify the service name targeted during the attack.
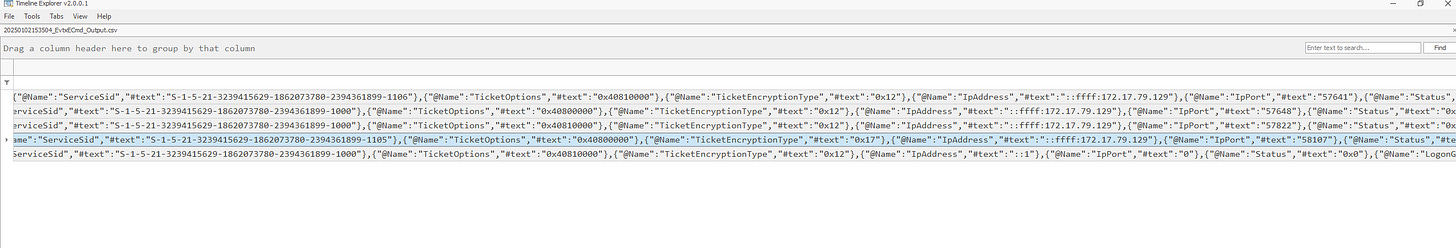
3. Identifying the Workstation’s IP Address
Approach:
Continue using the logs filtered for Event ID 4769 and relevant user accounts.
Locate the Payload field that contains the IP address of the originating workstation.
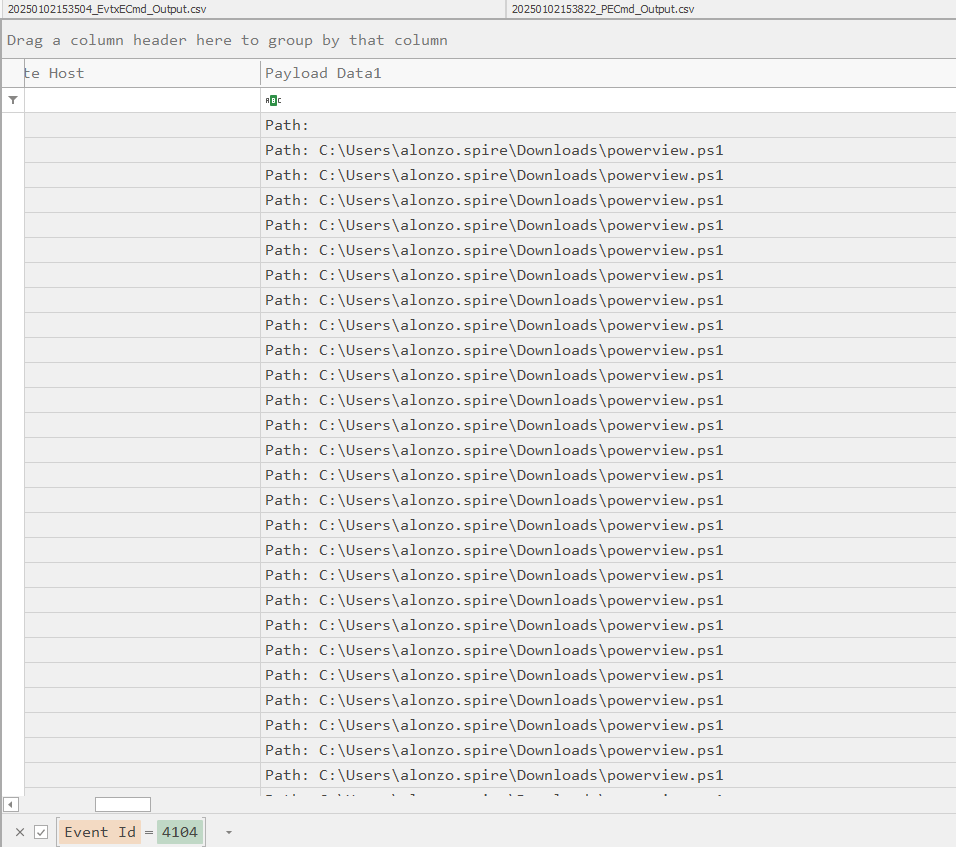
4. Identifying the Enumeration Script for Active Directory Objects
Approach:
Analyze the PowerShell logs from the workstation using EvtxECmd to parse and load them into the Timeline Viewer.
Look for a suspicious PowerShell script execution that enumerates Active Directory objects and identifies Kerberoastable accounts.
A quick web search of the script name may help confirm its purpose.
5. Determining the Script Execution Time
Approach:
From the PowerShell logs, filter for the execution details of the identified script.
Note the timestamp to confirm when the script was executed.
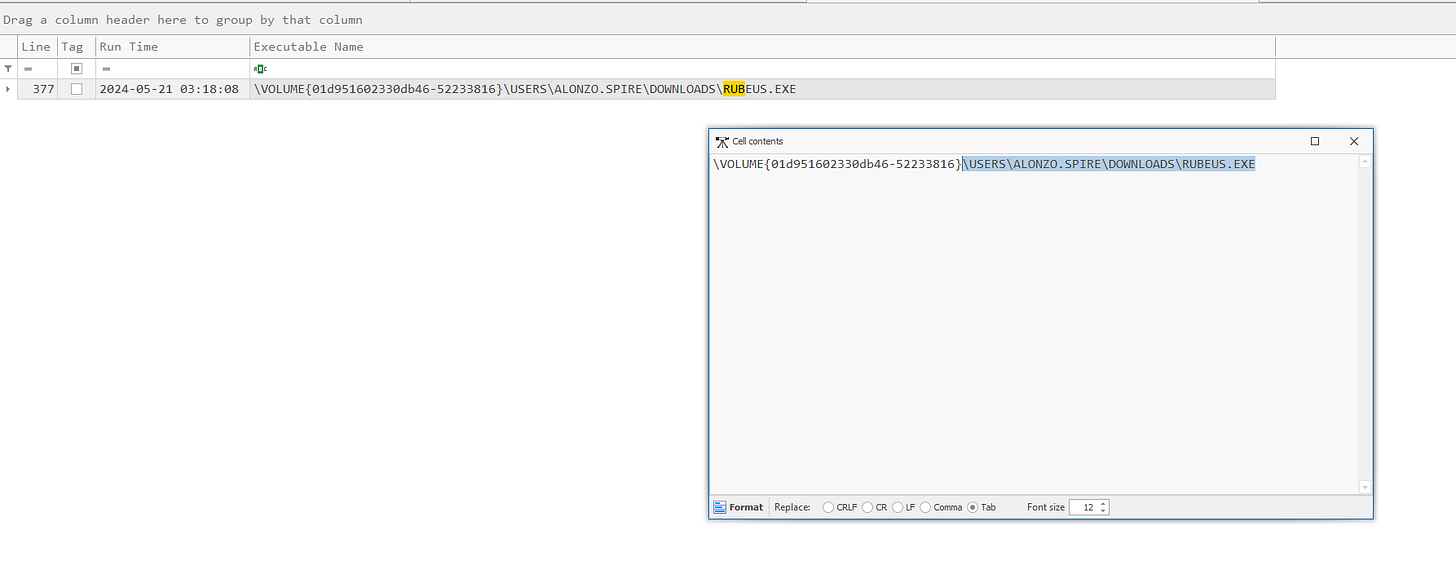
6. Locating the Tool Used for the Kerberoasting Attack
Approach:
Refer to the Prefetch Files processed through KAPE’s PE Logs module.
Identify the binary/tool responsible for the Kerberoasting attack.
The full path of the tool can be extracted from the logs.
7. Determining When the Credentials Were Dumped
Approach:
Use the same Prefetch File logs as in Question 6.
Identify the execution timestamp of the Kerberoasting tool by cross-referencing with the log timeline.
By following the outlined steps and leveraging tools like EvtxECmd, Timeline Viewer, and KAPE, this process allows for a thorough investigation and confirmation of the Kerberoasting attack within the network.