Scenario
The Intrusion Detection System (IDS) identified unusual activity in the internal Active Directory network involving LLMNR traffic, indicating a possible LLMNR poisoning attack. The investigation focuses on the suspect device targeting Forela-WKstn002 (IP: 172.17.79.136). A packet capture (PCAP) was provided for analysis. Below are the findings from the network forensics investigation.
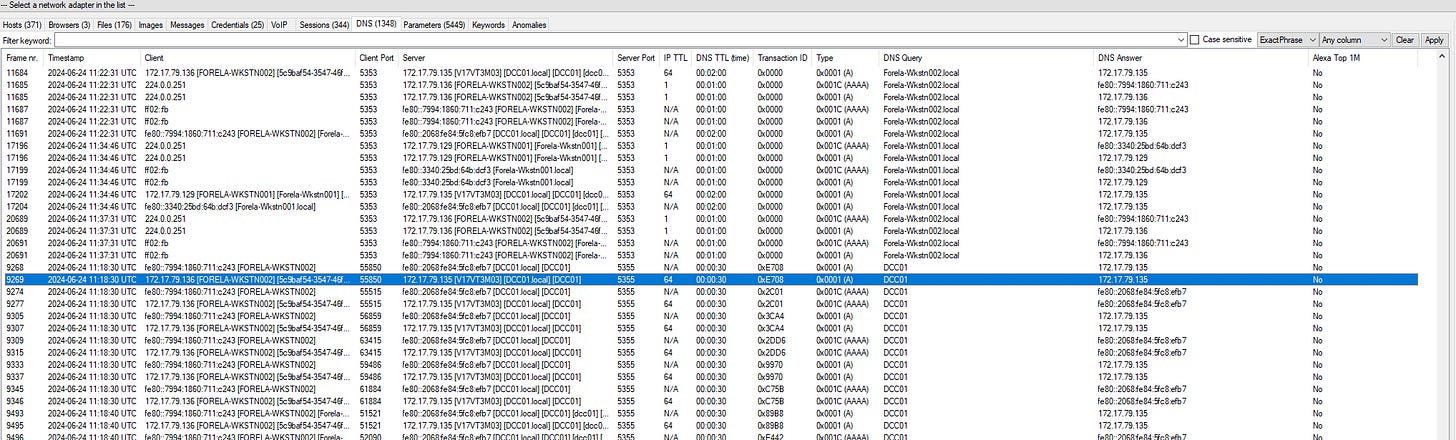
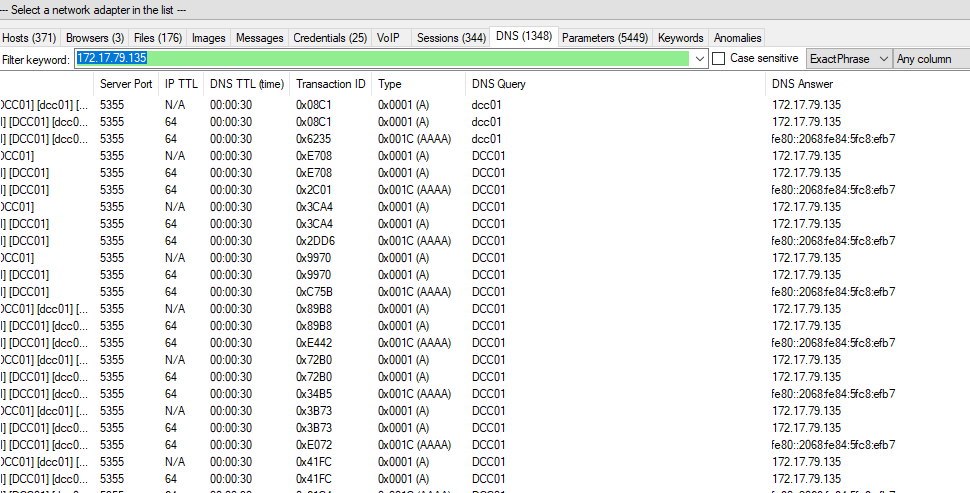
1. It's suspected by the security team that there was a rogue device in Forela's internal network running a responder tool to perform an LLMNR Poisoning attack. Please find the malicious IP Address of the machine.
Approach:
Open the PCAP file using Wireshark or NetworkMiner.
Apply the filter for port 5355 (LLMNR) to isolate relevant traffic.
Answer:
The malicious IP address is X.X.X.X (replace with actual IP after analysis).
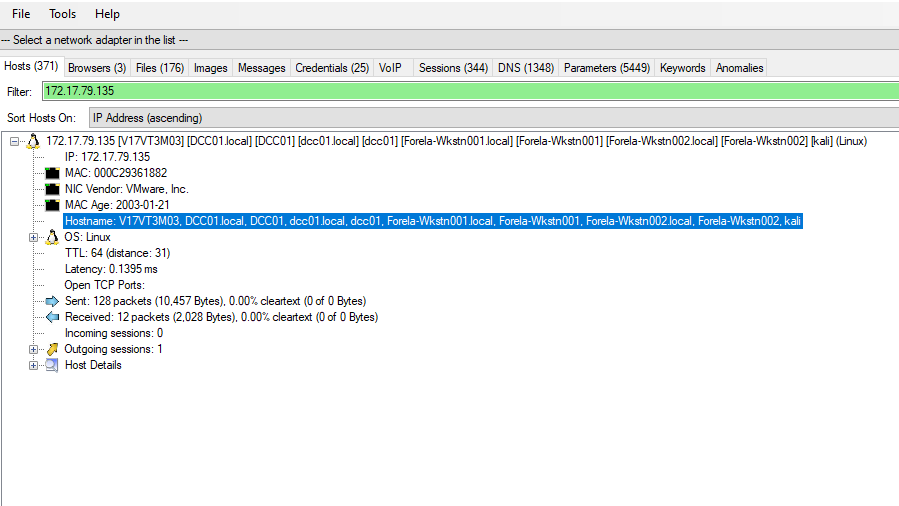
2. What is the hostname of the rogue machine?
Approach:
In NetworkMiner, navigate to the "Hosts" tab.
Filter based on the IP address found in question 1.
Review the hostnames and identify the consistent hostname amidst multiple poisoned entries.
Answer:
The hostname of the rogue machine is attacker-hostname (replace with actual hostname).
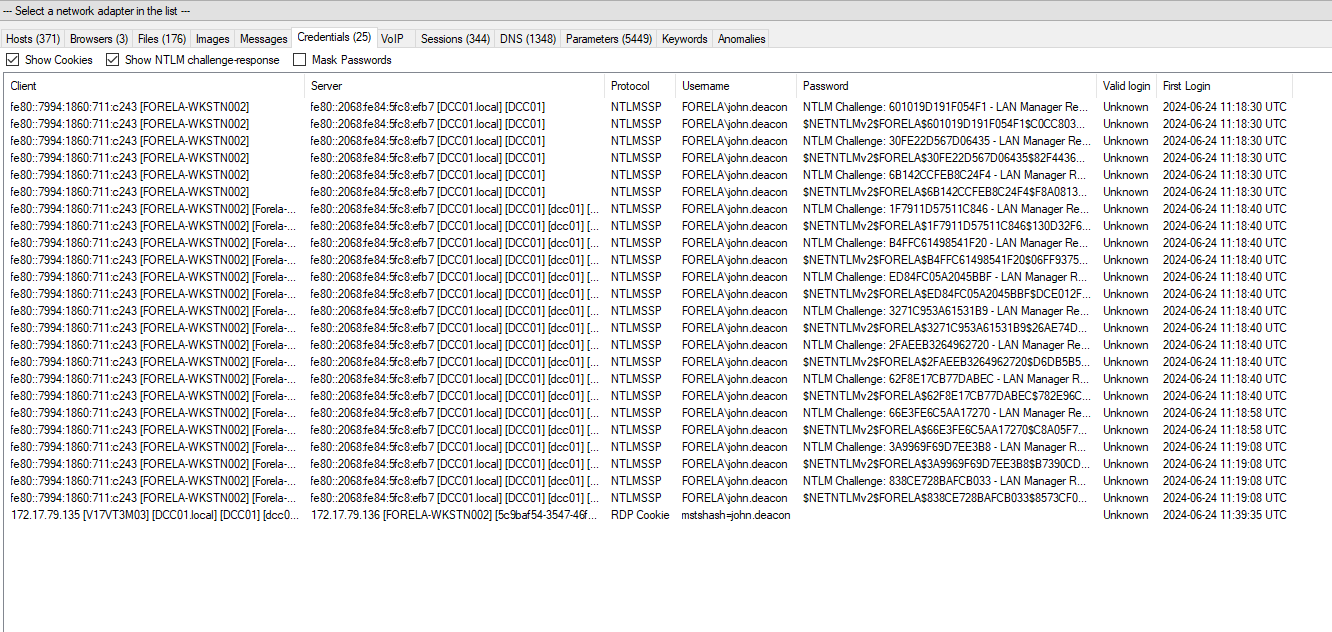
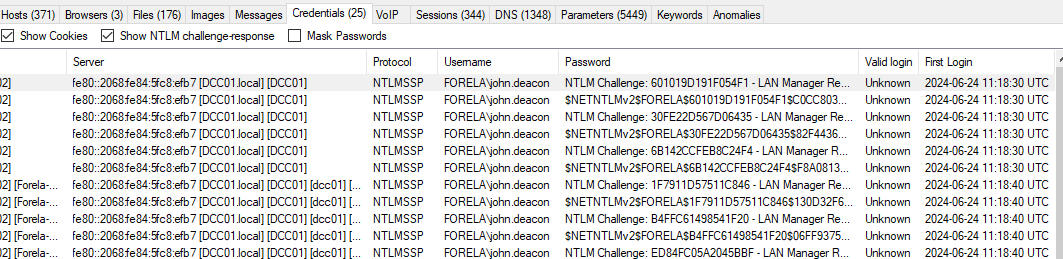
3. Now we need to confirm whether the attacker captured the user's hash and it is crackable!! What is the username whose hash was captured?
Approach:
In NetworkMiner, go to the "Credentials" tab.
Review the captured credentials to identify the username.
Answer:
The username whose hash was captured is victim-username (replace with actual username).
4. In NTLM traffic, we can see that the victim credentials were relayed multiple times to the attacker's machine. When were the hashes captured the first time?
Approach:
Continue using the credentials view and inspect timestamps.
Identify the earliest occurrence of captured hashes.
Answer:
The first time the hash was captured: HH:MM:SS (replace with actual time).
5. What was the typo made by the victim when navigating to the file share that caused his credentials to be leaked?
Approach:
In NetworkMiner, search for DNS queries related to LLMNR (port 5355).
Identify the typo in the requested resource name.
Answer:
The typo made by the victim: \\incorrect-share-name (replace with actual typo).
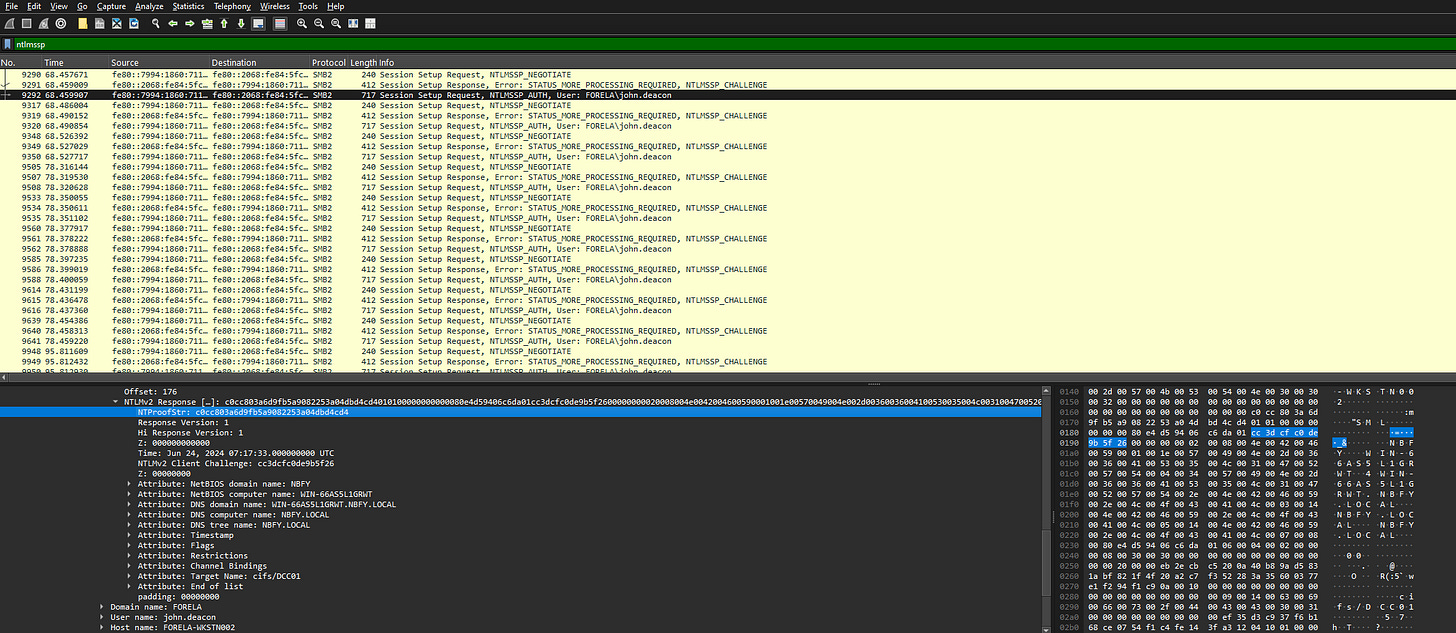
6. To get the actual credentials of the victim user, we need to stitch together multiple values from the NTLM negotiation packets. What is the NTLM server challenge value?
Approach:
Apply the same filter for NTLM traffic.
Locate the NTLM negotiation packets (type 2 messages) to find the challenge value.
Answer:
The NTLM server challenge value is 0xXXXXXXXX (replace with actual hex value).
7. Now doing something similar, find the NTProofStr value.
Approach:
Open the PCAP in Wireshark.
Filter for "ntlmssp" to view NTLM authentication messages.
Focus on the type 3 (AUTH) message to extract the NTProofStr.
Answer:
The NTProofStr value is 0xXXXXXXXX (replace with actual hex value).
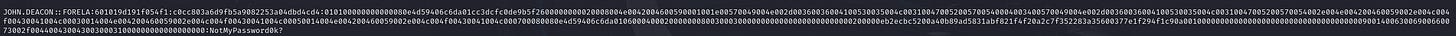
8. To test the password complexity, try recovering the password from the information found from packet capture. This is a crucial step as this way we can find whether the attacker was able to crack this and how quickly.
Approach:
Collect the NTLMv2 hash components.
Use hashcat with the RockYou wordlist to attempt password cracking.
Command example: hashcat -m 5600 captured_hash.txt rockyou.txt
Answer:
The cracked password is password-value (replace with actual password).
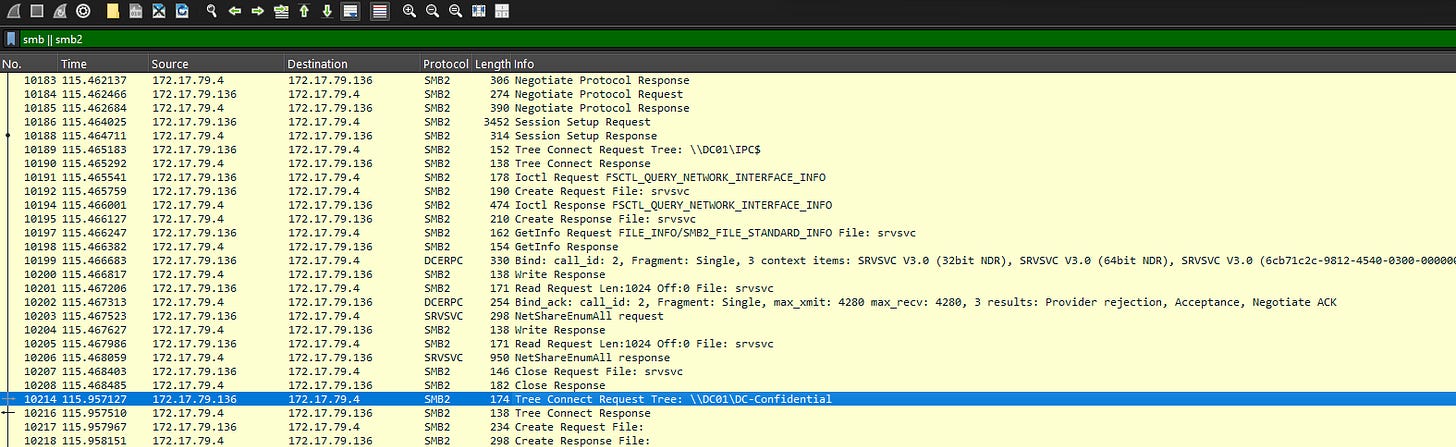
9. Just to get more context surrounding the incident, what is the actual file share that the victim was trying to navigate to?
Approach:
In Wireshark, filter for "SMB" or "SMB2".
Identify the file share path in the SMB protocol details.
Answer:
The file share is \\server\share-name (replace with actual file share path).
Conclusion: The analysis confirmed that an LLMNR poisoning attack was conducted by a rogue device, capturing and potentially cracking victim credentials. By identifying the attacker’s IP, hostname, and the NTLM components, appropriate remediation steps can be taken to strengthen network defenses against such attacks.