Category: Forensics
Difficulty: Easy-Medium
Goal: Investigate a PCAP file to trace a data breach involving brute-force FTP access, data exfiltration, and S3 bucket compromise.
Scenario
Forela recently experienced a serious data breach. Approximately 20 GB of sensitive data were stolen from internal S3 buckets. The breach began with the compromise of an FTP server, which led to further unauthorized access and eventual data exfiltration. You're provided with a PCAP file to analyze and determine what happened.
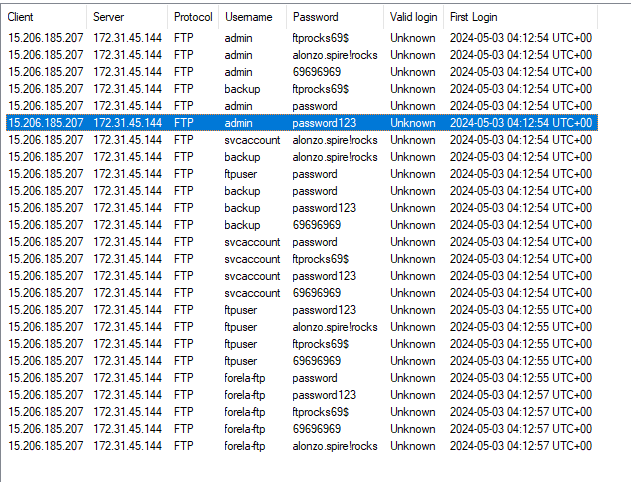
1. What is the attacker's IP address?
Tool used: NetworkMiner
How: Open the PCAP in NetworkMiner and check the Credentials tab.
Answer:
2. What city is the attacker from?
Tool used: IP2Location / online geolocation services
How: Look up the IP address
Answer: Mumbai
3. Which FTP application was used by the backup server? (Format: Name Version)
Tool used: NetworkMiner
How: In the Parameters tab, identify the FTP client application and version.
Answer:
4. When did the brute force attack start?
Tool used: NetworkMiner
How: Check the Credentials tab for the first FTP login attempts from the attacker IP.
Answer:
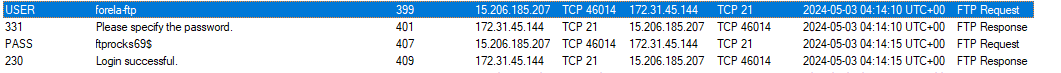
5. What are the correct credentials that gave the attacker access? (Format: username:password)
Tool used: NetworkMiner
How: Review the Parameters tab for the successful login session.
Answer:
6. What is the FTP command used to download the remote files?
Tool used: NetworkMiner
How: In the Files tab, look at the commands used in the FTP session.
Answer:
7. What is the password for the backup SSH server?
Tool used: NetworkMiner + file inspection
How: Right-click and open the file from NetworkMiner
Answer:
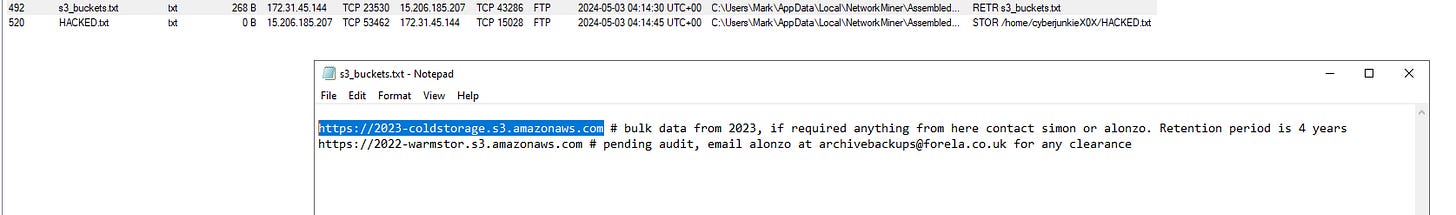
8. What is the S3 bucket URL for the data archive from 2023?
Tool used: Open the file s3_buckets.txt in NetworkMiner
How: Look for URLs referring to the 2023 archive.
Answer:
9. What is the internal email address used by the attacker in the phishing email?
Tool used: NetworkMiner
How: Again, in s3_buckets.txt, note the email address listed for clearance.
Answer:
Summary
Initial Entry: FTP brute force
Attacker IP City: (Mumbai)
Data Exfiltration: Done via FTP RETR command
SSH Access: found in plaintext note
Sensitive S3 URLs & Email: Extracted from s3_buckets.txt
Tools Used:
NetworkMiner
Online IP Geolocation tools