Objective:
Forela's internal security team conducted penetration testing on their networks. Following the tests, it was discovered that a host may have been compromised. The goal of this investigation is to verify how the compromise occurred using the retrospective collection provided.
1. What is the name of the repository utilized by the Pen Tester within Forela that resulted in the compromise of his host?
To address this question, we need to thoroughly examine the provided directories. Unzipping all contents, including those in subdirectories, is crucial, as it will give us access to the relevant repository that led to the host's compromise.
2. What is the name of the malicious function within the script ran by the Pen Tester?
The shell script is not directly available in the logs. To retrieve it, we must pull the script using git. Once obtained, examining its contents will reveal the name of the malicious function that was executed.
3. What is the password of the zip file downloaded within the malicious function?
In the script, a $PASSWORD variable is passed, which is constructed using $part1 and $part2. To determine the password, we need to identify the values of $part1 and $part2, possibly decoding them using a tool like CyberChef.
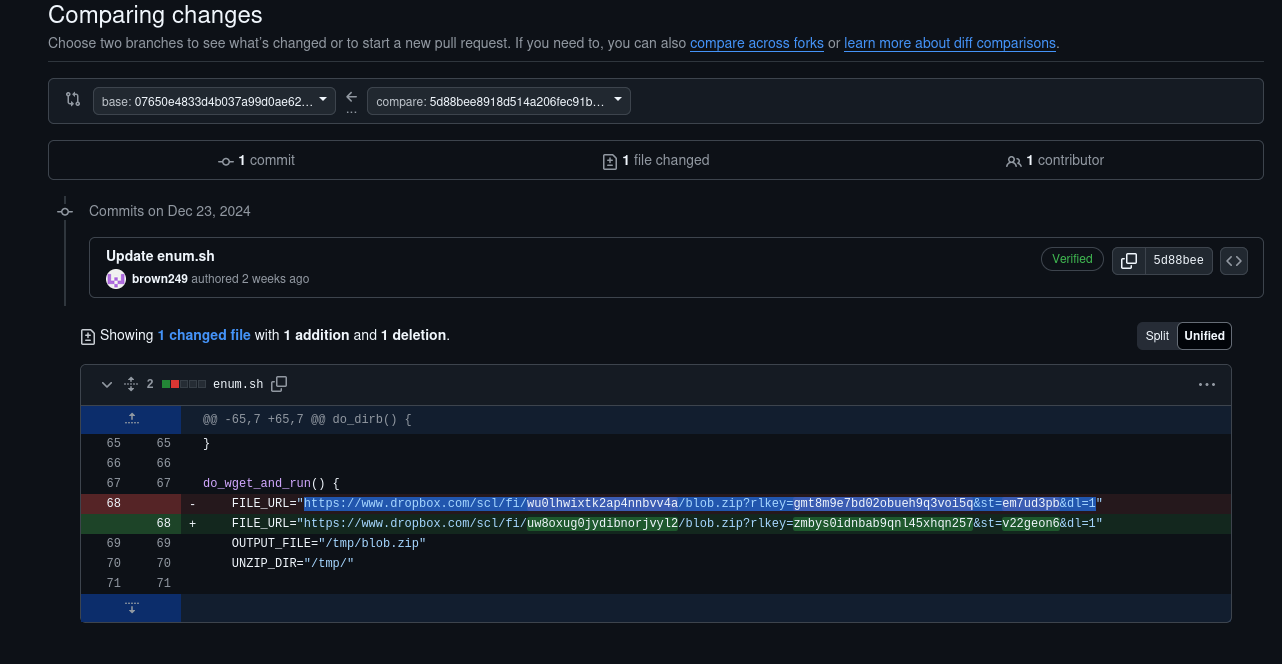
4. What is the full URL of the file downloaded by the attacker?
The function do_wget_and_run() is key to answering this question. By focusing on the variables f1 and f2, we can uncover the full URL that the attacker used to download the file.
5. When did the attacker finally take out the real comments for the malicious function?
To determine when the real comments were removed, we need to examine the history of the GitHub repository. This can be done by navigating to the "Activity" section on the GitHub repo, selecting the three dots, and comparing changes. By reviewing the deletions, we can pinpoint the specific change log, then pivot to Kali to run git commands and obtain the exact timestamp.
6. The attacker changed the URL to download the file, what was it before the change?
Using the same approach as in question 5, we can identify the previous URL by examining the version history and comparing changes to the repository.
7. What is the MITRE technique ID utilized by the attacker to persist?
Upon reviewing the script, we observe the attacker scheduling a cron job. This action points to a persistence mechanism, which corresponds to a specific MITRE technique ID related to cron job manipulation.
8. What is the name of the technique relevant to the binary the attacker runs?
We need to investigate the binary that the attacker executed. By examining the binary's attributes and behavior, we can determine the specific technique employed by the attacker related to the execution of the binary.
This write-up outlines the steps necessary to analyze and confirm the details of the compromise. By following the steps above, we can systematically answer each question and determine how the host was compromised.