Here's the revised write-up for the HackTheBox: RogueOne challenge without including the answers:
HackTheBox: RogueOne Write-Up
Scenario:
Your SIEM system generated multiple alerts in less than a minute, indicating potential C2 communication from Simon Stark's workstation. Despite Simon not noticing anything unusual, the IT team had him share screenshots of his task manager to check for any unusual processes. No suspicious processes were found, yet alerts about C2 communications persisted. The SOC manager then directed the immediate containment of the workstation and a memory dump for analysis. As a memory forensics expert, you are tasked with assisting the SOC team at Forela to investigate and resolve this urgent incident.
Task 1: Identify the Malicious Process and Confirm Process ID of Malicious Process
Steps:
Extract the memory dump:
7z x RogueOne.zip
Use Volatility 3 to analyze the memory dump:
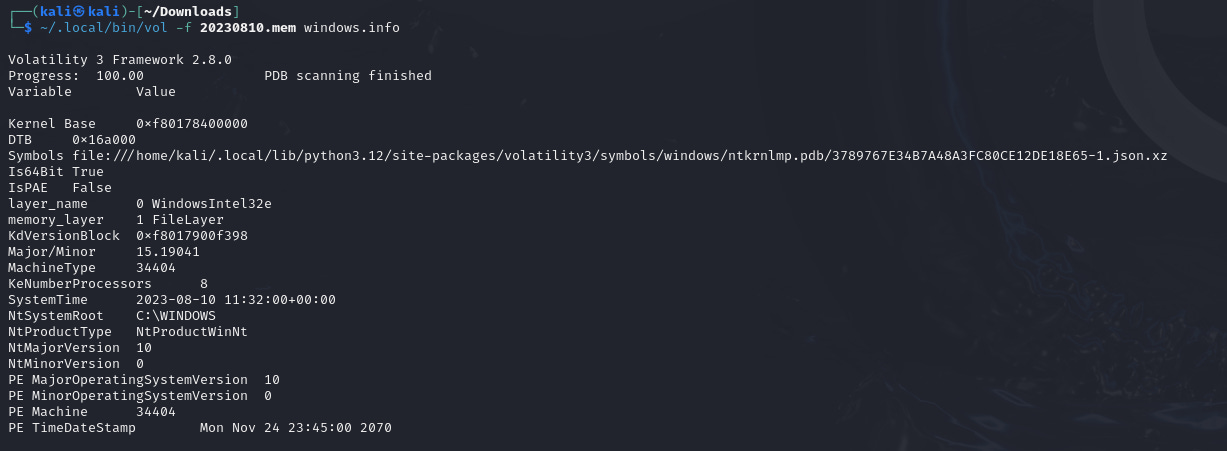
~/.local/bin/vol -f <memory-file> windows.pslist
Task 2: Identify the Child Process Spawned by the Malicious Process
Steps:
Run the windows.pstree plugin to check the process tree:
~/.local/bin/vol -f <memory-file> windows.pstree
Observe the parent-child relationship and note the process ID (PID) of the child process spawned.
Task 3: Find the MD5 Hash of the Malicious File
Steps:
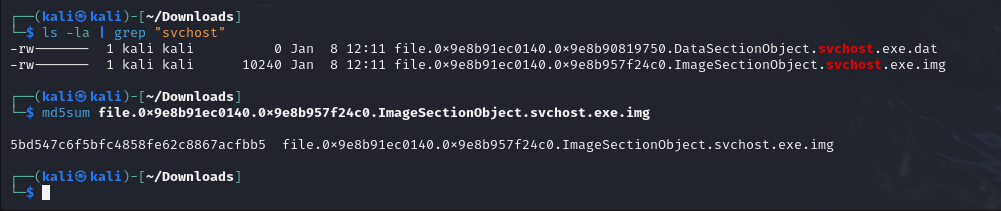
Dump the memory region of the malicious process:
~/.local/bin/vol -f <memory-file> windows.dumpfiles --pid <malicious-pid> -o .
Use
md5sumto calculate the hash:
md5sum <dumped-file>
Task 4: Confirm the C2 IP Address and Port
Steps:
Run the windows.netscan plugin to check for active connections:
~/.local/bin/vol -f <memory-file> windows.netscan
Look for the malicious PID and note the foreign address and port.
Task 5: Confirm the Execution Time and C2 Channel Establishment Time
Steps:
Use the windows.netscan plugin output.
Review the timestamp associated with the connection established by the malicious process.
Task 6: Find the Memory Offset of the Malicious Process
Steps:
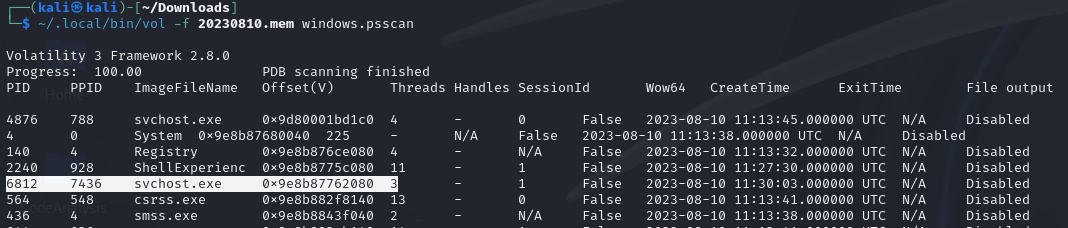
Run the windows.psscan plugin:
~/.local/bin/vol -f <memory-file> windows.psscan
Locate the malicious process PID and note its memory offset.
Task 7: Determine When the Malicious File Was First Submitted to VirusTotal
Steps:
Copy the MD5 hash from Task 3.
Open VirusTotal (
https://www.virustotal.com
) and paste the MD5 hash in the search bar.
Review the "First Submission" date and time.
Conclusion:
Following these steps allows you to systematically identify the malicious process, its behavior, and its timeline, helping the DFIR team perform root cause analysis and containment. Each tool used plays a critical role in building the timeline and gathering forensic evidence for further investigation.